Gender & Sexual Cyberviolence: An Exploratory Cross Cultural Inquiry
Editor's note: PBJ Learning is proud to provide a platform for Julian Siita's thesis on gender and sexual cyberviolence. It is a woefully understudied issue that is affecting everyone with access to the Internet. Please reach out to the author at [email protected]
WARNING: The reality is that the Internet is a dangerous place, and we would be doing you a disservice if we edited certain real-life, reality-based terms out of these materials. Be aware there are many terms in here that could be troubling, triggering, or “not suitable for youth,” so please use your discretion as you continue. There is quite honestly no way to prepare someone for a discussion about this topic without difficult terms, so be prepared.
SIITA Julian Saaka
DLMA
GENDER & SEXUAL CYBERVIOLENCE: AN EXPLORATORY CROSS CULTURAL INQUIRY
Thesis supervisor: Dr. Jose Alcaraz
« I hereby declare that this dissertation is the result of personal work and that any direct or indirect reference to the work of third parties is expressly indicated. I remain solely responsible for the analyses and opinions expressed in this document, which are not representative of the views or position of ESDES »
Acknowledgements
Firstly I would like to thank my thesis supervisor Dr. Jose Alcaraz for constantly encouraging me throughout this process. It was a challenge and he cheered for me every step of the way.
Secondly, I would like to thank The Kahiigis, Mr. Kuruvilla, Dr. Zawedde and Aunt Vivian without whom this thesis would not be possible.
Lastly I would like to thank my parents, my mother Sarah Nantongo for her prayers and my late father James Saaka who would have been beaming throughout this.
SUMMARY
Part 1: Literature Review
1. Feminism
2. Patriarchy
3. Resistance
4. Conclusion
Part 2: Field study
1. Overview
2. Context of the study
3. Case study data
4. Data analysis
5. Presentation of results (Stop Fisha)
6. Presentation of results (WOUGNET)
Part 3: Discussion
Introduction
1. Association Stop Fisha
2. WOUGNET
List of acronyms and abbreviations
Term | Definition/ Full Version |
WOUGNET | Women of Uganda Network |
DDA | Digital Dating Abuse |
CVAWG | Cyber violence against women and girls |
Introduction
The increasing reach, aim and ever insinuating nature of the internet and its intricate web of technologies has made sure we are all more connected than ever. In the click of a button and the swipe of a finger, we can have a front row seat to each other's lives online. In fact, the 2020 coronavirus pandemic which grounded people and organisations' lives alike, the necessity of our presence online increased internet usage to 50% to 70% (Beech, 2020).
The (European Union Agency for Fundamental Rights, 2014) found that 1 in 10 women has experienced cyber harassment since 15 so it is clear that cyber harassment is not a new problem. However, with increase of access comes increase in the occurrences of cyber harassment and cyberviolence. This threat of cyber violence looms over women's presence on the internet. In a study commissioned by the European Parliament, 15% of women said they had experienced some form of cyber harassment (Wilk, 2018).
(European Institute for Gender Equality, 2017) reports that women and girls are a particularly vulnerable demographic to the scourge of gender and sexual cyberviolence. One in three women will have experienced a form of violence in her lifetime, and it is further estimated that one in ten women have already experienced a form of cyber violence since the age of 15. However, some women and organisations are fighting back. This aim of this thesis is to examine the portrayal of gender and sexual cyber violence within the context of two organisations; a French non-profit organisation (Association Stop Fisha) and a Ugandan non-governmental organisation (WOUGNET) and to understand how cyberviolence is tackled by these organisation through their different activities. Through a thematic analysis of visual and written data collected from one organisation's social media accounts and book and interview transcripts with the employees of the other, I will explore the following questions:
1) How do the organisations portray gender and sexual cyberviolence?
2) What activities are they employing against gender and sexual cyberviolence?
To further this, an exploratory examination was conducted by interview into a similar non- governmental organisation in the Global South known as Women of Uganda Network, to compare and contrast the similarities and differences in both the portrayal and fight against gender and sexual cyberviolence. (Thomas and Davies, 2005) mentioned that debates within feminist theory around the subject of resistance and when it was seen to count have led to the emergence of a more nuanced and varied conception of resistance. In this way, the organisations' activities can be seen through the lens of resistance against cyberviolence. In another context, women's attitudes and actions in the workplace have been shown as made up of nuanced commitments and resistances to context-relevant identity issues. Therefore, they are not entirely individual and private nor entirely collective and public (Aldossari and Calvard, 2021). Both of these lead to an understanding that resistance does not have to be overt to count and can be more subtle.
To understand the context of gender and sexual cyberviolence, a literature review was conducted on the definition and history of feminism, with a breakdown on the different waves of feminism. Following this, an exploration of feminist theory in relation to patriarchy, sexual violence and resistance was conducted along with an evaluation of past studies of cyberviolence. For this thesis, the focus was to gain an understanding of the how two different organisations (one in the European context and the other in the Global South) portrayed cyberviolence and their activities to combat it in relation to resistance.
Part 1: Literature Review
1. Feminism
There is no one definition of the word feminism because it has evolved according to what was being resisted against. Indeed in (Thomas and Davies, 2005) it is quoted from (Weedon, 1987:1) that the word feminism denotes a politics that is synonymous with causing trouble, critique and change. (Ward et al., 1999) also states that feminism is a troublesome term that encourages people to express opinions, however it can be unclear what is being talked about, due to limited knowledge or prejudiced misrepresentations.
1.1 Introduction
The problem then, according to (Ward et al., 1999) remains that feminism, despite its diversity in discussions had its centre often rooted in the single entity of equality. (Ward et al., 1999) continues to note that because there have always been differing approaches, those wishing to gain a handle of its meanings came face to face with obstacles in understanding it.
For our study, it serves as a broad starting point in which to consider the concept of gender and sexual cyber violence.
1.1.1 The First Wave of Feminism
This period featured Mary Astell who was considered one of the earliest true feminists, as she was the first English writer to explore and assert ideas about women which are still recognisable today. Though she was conservative, she advocated for the women's freedom from the conventions of the time (such as marriage) that resulted in underdeveloped and untrained minds. Her negativity toward men and marriage did not endear her to many women readers(Walters, 2005).
(Walters, 2005) added that Astell's argument was that women were just as capable as men in spite of a lack of training to cultivate and improve them. She was a big supporter of other women and encouraged women to take their lives and selves seriously. This came through trusting their own judgement and choosing their own way in life whether that meant education or other means of development.
Another key figure cited by (Walters, 2005) was Mary Wollstonecraft, who argued for women to be given the chance to enhance their intelligence. She argued that femininity was a class based construct with artificial foundations. The fact that girls learned to be women when they were barely out of diapers, an exploitation of this femininity was their only option. To remedy this she proposed better education for girls, and a novel departure for her time: universal education, until at least 9 years old.
1.1.2 The Early 19th Century
(Walters, 2005) states that although William Thompson and John Stuart Mill penned two of the best-known 19th-century arguments for women's rights, the authors both made sure to acknowledge their wives who actually inspired their ideas.
(Walters, 2005) mentions John Stuart Mill's 1869 publication The Subjection of Women, as a key examination into why treating women as less than was wrong and a death sentence to the improvement of human beings. She further mentioned that he was influenced by his wife Harriet Taylor, who was already married with 2 small sons when they met in 1830. They would eventually marry in 1851, 2 years after the death of her husband and a friendship of almost twenty years between them.
William Thompson's views on marriage were expressed in his book addressed to and inspired by Anna Wheeler. She had become known for her reform movement interest upon her return to London two years after the death of her husband. In her case, she left her husband who was a drunkard. Thompson's book delved into the married woman's plight as being only viewed as the property and pliant servant of the man she is married to (Walters, 2005). It referred to her home as a “prison house” emphasising that everything in it including his breeding machine, the wife belonged to him. It likened married women's situation to that of slaves located in the West Indies(Walters, 2005).
At this time, mothers did not have rights over their children and family property, instead being treated like a servant. Despite the modern feminist criticisms that these writings focused only on married women and no single women or daughters, the vulnerability of married women having no legal existence in this period was dangerous(Walters, 2005).
(Walters, 2005) states that by the mid-19th century, other women like Frances Power Cobbe were taking up the fight for better education and the issues faced by both single and married women. Cobbe spoke about the women in miserable marriages and campaigned for a Married Woman's Property Act.
(Walters, 2005) adds that across the pond in America, the feminism movement was borne out of the anti-slavery movement which began to take root in about 1830 despite some of these groups being whites only. She mentions a key figure, Sojourner Truth who was a former slave that rejected the idea that women needed men's protection and spoke out against the right to vote being awarded to former male slaves who were freed post-Civil War. Women were granted the right to vote in 1920 and all black people in 1970.
The key issues at this time were the legal existence of married women in relation to property and their children and the right to vote.
1.1.3 The Late 19th Century
In the late 19th Century, a more defined women's movement began to emerge in England around issues such as women's need for better education and increased options for employment. This was initiated through campaigns organised by Barbara Leigh Smith and a group of her friends who came together as a reaction against the fact that a Victorian woman's highest virtue seemed to be constrained by a narrow definition of femininity(Walters, 2005). Women were generally expected to be passive and a woman born into the middle class maybe had the chance to earn a terrible living with few other options available.
If a woman was unhappily married there was no way out and despite some women having impressive achievements, they still shied away from speaking about the emerging feminism of the period. The Contagious Diseases Acts which was a significant campaign, sparked a wider conversation about women's rights and autonomy over their own bodies because it created dissent, thus shedding light on the need for equal treatment and the recognition of women's agency in matters of sexuality (Walters, 2005).
It was stated by (Walters, 2005) that this campaign not only shed light on the cruel and hypocritical double sexual standard of society but also had far-reaching implications. The first of these Acts was passed in 1864, granting the police the power to apprehend any woman suspected of engaging in prostitution in certain ports and garrison towns. These women would then be subjected to invasive internal examinations, often using brutal methods, and if found to have any signs of venereal disease, they would be confined to hospitals. Subsequent extensions to the Act were made in 1866 and 1869.
(Walters, 2005) mentions that as the implications and injustices of these Acts became apparent, women began to voice their opposition with notable figures such as Elizabeth Garrett, Florence Nightingale, and Harriet Martineau joining the protest and arguing against the regulation system that targeted women. The campaign against the Contagious Diseases Acts exposed the deep-rooted inequalities and injustices within society, particularly in regards to sexuality and gender. It challenged the prevailing notion of a double standard, whereby men engaging in prostitution were not subjected to the same scrutiny and punishment as women.
(Walters, 2005) reports that in 1869, a Ladies National Association for the Repeal of the Contagious Diseases Act was set up becoming the first group of respectable women to be able to effectively apply pressure. First, they started on the brutal laws against prostitutes or those suspected of prostitution and then later as the right to vote became more important. Not only was it seen as symbolical recognition of full citizenship but it was also the most practical way to effect changes and push forward reforms.
(Walters, 2005) describes this campaign for the right to vote as the Women's Suffrage Movement which would eventually lead to success in the United States in 1919. She adds that in other countries like New Zealand and Australia, women were granted the right to vote in the 1890s, with participation in Federal Elections being granted in 1902. Denmark granted this right in 1915, and the Netherlands in 1919.
Key fights here were still advancement of women's education and the right to vote.
1.1.4 Early 20th century Feminism
(Walters, 2005) mentions that after English women achieved legal and civil equality, the movement was divided on whether the next fight should be for the same terms of equality as men or to focus on women's other needs and problems.
In addition, because the effects of the First World War provided women with the chance to work outside the home with over a million women working in munition factories, engineering, hospital, this brought forth the demand for pay rises and equal pay to that of men (Walters, 2005). However, due to the war a lot of women became widows or remained unmarried.
1.1.5 Second Wave Feminism
Post Second World War brought about what is sometimes referred to as ‘second-wave' feminism in multiple countries. This was marked by the United Nations established a Commission on the Status of Women and then issued a Declaration of Human Rights two years later, which confirmed men and women's equal rights as to marriage, during marriage and at its dissolution as well as women having a right to special care and assistance in their role as mothers (Walters, 2005).
In fact, (Walters, 2005) further reports that feminism was acknowledged by the UN during three international conferences on women's issues in Mexico City, Copenhagen and Nairobi between 1975 and 1985, with it being noted that the differences in women from different from different regions, classes, nationalities, and ethnic backgrounds. It became clear that different women had various concerns and killed the myth of sisterhood that assumed all women shared identical interests.
It was also during this wave that more Western women continued to write on the topic, a notable one being Simone de Beauvoir whose writings explored a woman's experience. Beauvoir explored the concept of male activity being considered more valuable and important than Nature and Woman. In addition, (Walters, 2005) she stated that women had never been considered fully human, having been denied the right to create and find meaning in projects outside of their role in relation to the man. She identified this as being “Other” and seen as an object by and for men. So many different women identified with this especially in noting the similarities in personal frustrations towards the general conditions of women.
This movement also brought to the forefront issues of intersection between race and feminism through the writings of people such as Bell Hooks in her Feminist Theory: From Margin to Centre (1984), which stated that the feminism of the time was racist and that the women who were the most victimized by sexist oppression were not allowed to speak out. It called to attention those who had been disillusioned.
Another notable issue during this period was a woman's right over her own body. Because a woman's looks and appearance was consistently correlated to her value, this issue seemed minor at first. It was and still is consistently reinforced through images in the media that show us an unattainable standard of beauty to aspire to, a standard that even the people in those pictures do not meet themselves. Western Feminists were concerned by how these images caused a desperate chase after the latest fashions leading some to resort to even more dangerous methods such as dieting (through anorexia, bulimia and restrictive eating) or even continuous self-mutilation through plastic surgery (Walters, 2005).
1.2 Beyond Western Feminism
From the paragraphs above, it is clear that there has never been just one issue plaguing women. Whether it is the advancement of education, property rights, the right to vote or equality and anti-discrimination, feminism has come a long way and will exist for as long as world shifts create more issues and inequalities. It is important to note that while Western Feminism receives majority coverage, women in other parts of the world deemed less important or less developed have also had to contend with similar if not harder problems. These problems have been exacerbated by beliefs of their ethnic groups, caste, and religion often being complicated by a struggle for an establishment of democratic government and for more basic freedoms (Walters, 2005). In places such as Latin America, Africa and Asia and the Middle East, where generations of women's lives have been affected by colonialism and neo-colonialism, feminism takes on a different flavour and the struggles are often different than what has been expounded upon in the historical overview above. When we bring the focus to Africa, local beliefs have also about practices out of differences in class, religion, ethnic origins and all following behind the legacies colonialism left behind.
A brilliant penning by (Ebila and Uhde, 2020) recognizes the lack of opportunities for mutual discussions to occur between Africana and European feminist researchers as well as not enough open access to publish in. In addition, they mention that the information available on the lives of women in Eastern Africa is all over the place and often overshadowed by poverty as the issue at the forefront. by scholars and activists and from the critical media. However, we felt that there have. It is therefore even more important to recognise the marked differences in Western feminist movements and African feminist movements. Though research on feminism and gender in Eastern Africa has been going on for over three decades, access to research reports and literature is difficult although places like the School of Women and Gender Studies (founded in 1991) at Makerere University in Uganda are working to overcome this.
(Ebila and Uhde, 2020) gave a succinct summary of what African feminism involves, stating that it is varied and includes issues of mothering, gender relations, sisterhood, land ownership, farming, trade, peacekeeping, education, and how all these build the lives of girls and women in relation to the men in their lives to make life better for all. Quoting (Mikell, 1997) who stated that African feminism is not just about the political participation and leadership but everything – the bread, the butter, and power, and about how these things impact the lives of African women. (Ebila and Uhde, 2020) further clarify that the work of women in Eastern Africa not only contributes to improvement of living conditions but to the development of their immediate families and societies. By contrast (Goredema, 2010) states that African feminism concerns itself not only with the rights of women from Africa but is also inclusive of those living in the Diaspora as many of the contributors to the literature have often lived “abroad”. It is therefore limiting to let geographical location be a deciding factor as the name would imply. Instead we must understand that the debates, practices and implementation of African feminism are mostly pursued on the African continent. This means that despite difference in location (East, West, North and Southern parts of Africa), women all over Africa and within the diaspora cannot separate from the challenges (individually and collectively) against patriarchy, oppression and underdevelopment.
2. Patriarchy
(Napikoski, 2021) defines a patriarchy, through its origin from the ancient Greek patriarchs, as being a society where power was held by and passed down through the elder males. She adds that the description of a “patriarchal society,” is closely connected in that it reiterates the idea of males holding power and privilege: head of the family unit, leaders of social groups, boss in the workplace, and heads of government.
(Ortner, 2022) defines patriarchy as a social formation of male-gendered power with a particular structure that can be found with striking regularity in many different arenas of social life, from small-scale contexts like the family, kin groups, and gangs, up through larger institutional contexts like the police, the military, organized religion, the state, and more.
As it is ingrained in our society, we know that women have not been able to divorce themselves from experiencing its effects or even being influenced by it in a multitude of ways.
2.1.1 Patriarchy's influence on women
According to (Dickerson, 2013), living in a patriarchal culture provides men with certain privileges and entitlements that are not available to women including access to ways of being and performing that are closed to women. In addition, this same patriarchy influences women to respond in defined ways, often accommodating and deferring to male interests (Hare-Mustin & Marecek, 1988, 1990; Hare-Mustin, 2004; see also Coontz, 2012 as seen in Dickerson, 2013).
In understanding this, she continues by noting feminism shines a direct light on the effects of a patriarchal culture on women's lives and continues to critique male privilege. In the patriarchal structure, (Ortner, 2022) states that the women (and “wrong” kind of men) remain outsiders regardless of if they come “inside” without protection and sponsorship from those who are considered first class. In this way, they remain as a type of second class citizen (with lower pay, for example), and are as a result subject to endless harassment, up to and including rape.
(Ortner, 2022) mentioned the fight against second class citizenship was the focus of earlier feminist movements and feminists began to later understand that entrance into the “club” and reaping its benefits was not the only part of it. They ultimately needed to dedicate their focus to breaking up and disrupting the structure in place, the social organization of patriarchal power.
(Ortner, 2022) concludes that wherever patriarchy resides, the assumption is that its members, are all “superior men” or potential superior men, and which in turn excludes not only women but other men in those other categories who fail to meet this test. For the study, this point is important because men regardless of whether they are considered superior or not, ultimately use violence as a way to subjugate women.
2.1.2 Violence
Violence is defined by the World Health Organization as “the intentional use of physical force or power, threatened or actual, against oneself, another person, or against a group or community, which either results in or has a high likelihood of resulting in injury, death, psychological harm, mal development, or deprivation.”(WHO, 2002 as cited in Lokaneeta, 2016).
However, (Lokaneeta, 2016) states that this definition does not draw enough attention to the victims, perpetrators or the reasons behind the harm; rather it only captures the scope of harm associated with violence. In addition, this definition is not specific enough to accurately capture the nature of gender and sexual cyber violence.
It is thus important to understand that violence does not happen in a vacuum. (Lokaneeta, 2016) states that feminist scholars have sought to differentiate between the many forms of violence including that they exist on a continuum while keeping them framed in their specific context.
Through their studies, feminist scholars have examined the different roles states, non-state parties from dominant classes and communities and individual offenders have played in the endorsement of violence (Lokaneeta, 2016). The author continued by noting the existence of structural violence (suffering induced by economic and political forces, such as extreme poverty, unjust healthcare policy, slum demolition); representational and symbolic violence (discursive constructions that dehumanize and objectify some humans, while celebrating the “natural superiority” of others), and epistemic violence (forms of knowledge production that deny or undermine the agency and subjectivity of particular populations).
Scholars have also investigated and documented forms of racialized and gendered violence ignored in mainstream approaches, and developed path breaking works that address racialized violence (e.g., Middle Passage, branding, slave plantation, lynching, prison industrial complex) and gendered violence (e.g. rape, kidnapping, domestic violence, sexual harassment, feminization, forced sterilization). For this study, the focus will remain on violence directed towards women and girls.
2.1.3 Sexual violence
Sexual violence is a term that is defined as follows:
“Any sexual act, attempt to obtain a sexual act, unwanted sexual comments or advances, or acts to traffic … against a person's sexuality using coercion, by any person regardless of their relationship to the victim, in any setting, including but not limited to home and work.” (WHO, 2002, p.149 as cited in Powell and Henry, 2017, p.4)
It works as a more inclusive definition because it covers both physical acts e.g. rape and sexual assault but also offenses where there may not be any contact e.g. non-contact offenses and behaviours, such as sexual harassment and sexual coercion (Powell and Henry, 2017). In addition, the authors state that its widespread usage among academics, professionals and victim-survivors, shows that violence as not simply a physical act involving physical injury but also a psychosocial and structural problem.
Knowing that sexual violence is a structural problem, sexual violence cannot be referred to without acknowledging the long held debate by feminist scholars and commentators (Powell and Henry, 2017) over the existence of a rape culture, with some arguing that a rape culture is one that implicitly and explicitly condones, excuses, tolerates, normalises and fetishizes sexual violence against women).
This is important as it leads into the term ‘technology-facilitated sexual violence', a term used to encompass a diverse range of acts involving technology, drawing on the WHO definition (Powell and Henry, 2017). This term, though it will not be used through the thesis, encapsulates the context of gender and sexual cyber violence which is what the thesis will entail.
2.1.4 Women's experiences of sexual violence
(Powell and Henry, 2017) note that sexual violence (and gendered violence more broadly) is both a private and public harm because of the shame and taboo around being a victim of sexual violence. This means that an individual who has had this personal and private violation, most often perpetrated by a known man in a private, residential location is reluctant to report informally to family and friends or formally to the police. It adds to the silencing around the issue and the entitlement of husbands in various countries to their wives' bodies.
Women grow up being socialised to bear ‘everyday' intrusions, routine sexual harassment and sexual assaults in public spaces, with a much deeper fear than men of interpersonal violence in public space thus having to engage in behaviour to safely manage these situations during their day. Thus women's private and individual experiences of sexual violence also shape women's public and collective experiences of moving through a society in which their safety, and particularly their sexual autonomy, is uncertain (Powell and Henry, 2017).
It poses the question as to how this shows up in instances of cyberviolence, which occurs online, a place that can be considered another extension of the public domain.
2.1.5 Cyber violence
(Backe et al., 2018) report that the term cyberviolence emerged in the early 2000s, with the widespread diffusion of portable laptops and Web 2.0, with its meaning remaining highly contested and steeped in controversy (Grant 2016; Jeong 2015; Lenhart et al. 2016).
Broadly speaking, the concept of cyberviolence is meant to encapsulate the kinds of harm and abuse facilitated by and perpetrated through digital and technological means. The UN's adoption of the term in their 2015 Cyber Violence Against Women and Girls (VAWG) report brought about debate about the definition of cyber VAWG, because of its terminological overlaps with other forms of violence and crime, and the extent to which the term's attempt to capture all forms of online violence was either accurate or fair (Chisholm, 2006).
In their review, (Backe et al., 2018) held that there was a lack of consistent, standard definitions or methodologies used to conceptualize and measure cyberviolence. Most of the literature focuses on cyberbullying among heterosexual adolescents in high-income countries. Demographic data on perpetrators are limited, prevalence estimates are inconsistent, and almost no primary research has been conducted in low- and middle-income countries (LMIC). Cyberviolence is not only associated with negative psychological, social, and reproductive health outcomes but also it is linked with offline violence, disproportionately affecting women, girls, and sexual and gender minorities. There is an urgent need to develop a uniform set of tools to examine cyberviolence internationally. Future research should explore the gendered dimensions of cyberviolence and the continuum between online and offline violence, including in LMICs. (Backe et al., 2018) suggest that the various terminologies used to describe cyberviolence are similar but not necessarily interchangeable (IGF 2016), demonstrating a lack of consensus within the research community on how to define and categorize these digitally based behaviors and actions. The result is an intermeshing of categories following which they created a table showing the breaking down of the different forms of cyberviolence as shown on the next page.
Table 1. Cyberviolence Tactics
Tactic | Definition |
Defamation | the false statement of fact often used to damage the reputation of someone; can include slander or libel |
Doxing (sometimes spelled doxxing) | releasing identifiable, and often private, information about an individual online; can include name, phone number, email address, home address, etc. and result in in-person stalking or harassment, sometimes physical violence or threats |
Flaming | when a victim is belittled or demeaned on a live public forum (Pittaro 2011) |
Hacking | gaining access to someone's private computer or data stored via digital means, such as Cloud or other storage architecture |
Happy slapping | recording or filming an attack on a mobile phone |
Impersonation | creating an account using the name or the domain name of another person, often with the intent to harm, harass, intimidate, or threaten others |
Sexting | sending of sexually explicit messages or images by cell phone (Drouin et al. 2015), could be coercive in instances of intimate partner aggression |
Surveilance | using GPS to track the movements of someone via their phone or other wireless device; secretly monitoring texts, phone calls, emails, messages, etc. conducted on someone's personal accounts |
Trolling | trolls often commit intentionally inflammatory and divisive speech online (Mantilla 2015; Phillips 2015) |
Source: Backe et al., 2018, p. 137.
Table 1, shows a starting point from which to understand the portrayal of gender and sexual cyberviolence. Through reference the tactics that perpetrators can use to enact the different types of gender and sexual cyberviolence, an understanding of the vast landscape of the different types of gender and sexual cyberviolence. However, it may does not paint a complete picture of the new types that may crop up with the advancement of the technological landscape which may encompass several of the tactics shown.
In addition to this, (Backe et al., 2018) notes the variation and interchangeability of terms that are used in relation to cyberviolence as shown in the table below:
Table 2. Cyberviolence Concepts and Related Terminology
Cyberviolence term | Related terminology |
Cyberviolence | Online violence, digital violence, digital abuse, CVAWG, cyber abuse, cyber aggression, technology-related violence |
Online harassment | Electronic harassment, Internet harassment, cyber gender harassment, cyber/online sexual harassment, technology-related/CVAWG |
Cyberbullying | electronic bullying, Internet bullying, cyber aggression, online bullying |
CDA | cyber dating violence, electronic teen dating violence, online dating abuse, Internet partner cyber aggression, cyber teasing, DDA, electronic leashing |
Revenge porn | cyber rape, non-consensual pornography, involuntary porn, image-based sexual abuse |
Source: Backe et al., 2018, p. 137
From Table 2, it is clear that there is no one uniform term to which cyberviolence can be attributed. However, there is no inclusion of gender and sexual cyberviolence. The closest term is technology related cyberviolence which is similar to technology-facilitated sexual violence that was referenced in 2.1.3 above. Therefore it follows that with no set uniformity of terms, it will be sufficient to use the term gender and sexual cyberviolence throughout the study in reference to the different terms of technology facilitated/ related cyberviolence that will be explored.
3. Resistance
Without resistance, there would not be feminism. It was one of the most effective tools that the different movements throughout the years employed whether in subtle ways or in a more overt manner. Therefore, it is an important element of the literature review.
3.1.1 Resisting violence
When dealing with violence of any kind, an important piece of the discussion in the context of feminist studies is the resistance to it. This may take any form from political to the creation of forums to consider alternatives to violence, or the development of mechanisms to negotiate everyday life in a way that mediates the effects of such violence (Lokaneeta, 2016). As violence or the threat thereof has always been used to subdue different minority and disadvantaged groups, it gives an important backdrop through which to consider the question of how the different organisations portray the gender and sexual cyberviolence and the activities they do to offset this new form of violence.
3.1.2 Feminist theory and resistance
(Thomas and Davies, 2005) mentioned that the debates within feminist theory around the subject of resistance and when it was seen to count led to the emergence of a more nuanced and varied conception of resistance. However, before we get into these different definitions, (Thomas and Davies, 2005) provides a three way framework through which to view the feminist theory-resistance-organizational relationship as shown in Table 3.
Table 3. Three-way framing of the feminist theory—resistance–organization relationship
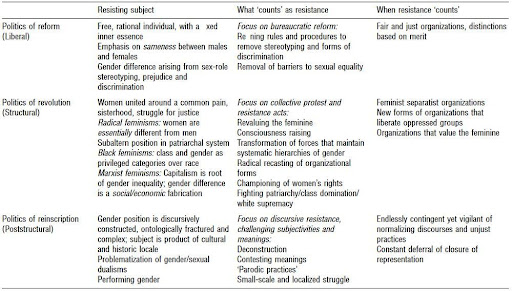
Source: Thomas and Davies, 2005, p. 715.
The authors followed up by highlighting the different definitions of resistance according to the different feminist perspectives as shown in the framework, most notably with this quote showcasing the Foucauldian feminist framework which took a micro- political understanding of the term resistance:
“Resistance to the dominant at the level of the individual subject is the first stage in the production of alternative forms of knowledge or where such alternatives already exist, of winning individuals over to these discourses and gradually increasing their social power.” (Weedon, 1999, p. 111 as cited in Thomas and Davies, 2005).
Within the structural approach, the authors stated resistance counts most notably with women speaking out and universally identifying other women's shared experiences. It was often defined as the construction of theory on women, for women by women. Therefore (Thomas and Davies, 2005) concluded that empowerment against resistance in this instance took shape by making the forms of oppression more visible and engaging in activities of consciousness-raising in order to turn an advantage for femaleness. The downside was that it was prone to silencing the voices of multidiverse participants.
By contrast, for Marxist feminists, gender difference is a social or economic struggle, and therefore not related to gender because they considered there to be no real differences between men and women. Radical feminists, on the other hand, were viewed as the source of resistance but with the view that the common oppression standpoint allowed women the distinctly advantageous viewpoint to expose the reality of gender subordination and to go beneath the surface of appearances (Hartsock, 1983 as cited in Thomas and Davies, 2005).
One of the important takeaways of the (Thomas and Davies, 2005) study was the explicit recognition that resistance within organization studies was mainly derived from studies on blue-collar workers, so subsequently there was a tendency to associate resistance with activities amongst this category of worker. Despite there being existing studies exploring professional and managerial resistance e.g. (Raelin, 1991; LaNuez and Jermier, 1994; Knights and Murray, 1995), in general managers and professionals were not usually considered because they do not traditionally fall under the categorization of oppressed.
Another was when (Thomas and Davies, 2005) stated that organization studies were increasingly discussing the shift of understanding resistance from more than just collective, overt activities to more subtle, every day, low-level forms of struggle and challenge. (Thomas and Davies, 2005) mentioned that the debates within feminist theory around the subject of resistance and when it was seen to count led to the emergence of a more nuanced and varied conception of resistance.
Thus the (Thomas and Davies, 2005) study was important for showcasing resistance in a group not traditionally focused on before i.e. social workers.
4. Conclusion
Before getting into the thesis topic, a review of the main concepts and definitions was important for an understanding of the importance of the topic and its origins. Before we understand gender and sexual cyberviolence, we must understand the roots of violence and sexual violence. Before we understand violence and sexual violence we must understand the fact that they are in fact tools of the patriarchy. Before we understand the patriarchy, we must understand feminism and its origins, by going through a different overview of the difference in rights women found themselves striving for overtime.
From reviewing the different sources, it is clear that although the definition of cyberviolence has been studied before, those studies were limited to mostly Western perspectives (United States, Canada, and United Kingdom) on the topic. The research featured in this review is limited in that it only shows the definitions of cyberviolence in the United States, Canada and Australia with no features from other countries located in Africa, Asia and Latin America. In addition, (Backe et al., 2018) added that the primary research conducted has had a youthful focus in regards to its samples and these may not be a good representation of the general population.
My study will introduce commentary of a new developed country not previously included in the aforementioned review and studies as well as and an organisation from a lower to middle income country (LMIC) in the Global South. This is important because the empirical data on cyberviolence in African countries is limited. It which will shed a comparative light on how two different organisations in Uganda and France portray gender and sexual cyberviolence differently (through their activities and approach) with a context of resistance. This will be examined in the context of the organisations' activities.
Through a thematic analysis, this thesis will show how two similar organisations that work to curb the same issue (gender and sexual cyberviolence). However it is important to note that this is only an introductory inquiry into the organisational perspective in two different countries.
Part 2: Field study
1. Overview
The first part of this section will consider the purpose of the case study and research questions, examine its context with reasons for selection of the case. Next, an in-depth narrative of the data collection in order to provide a closer look at the case and methods chosen. This will be followed by details of the data analysis, ethical considerations of the methodology and finally what changes and reflections occurred throughout the case study.
1.1 Qualitative research methods (case study):
From the form of the research questions, the aim of the research was to compare how two different organisations (Association Stop Fisha and WOUGNET) portray gender and sexual cyber violence including the activities they carry out against it and how they portray resistance through these. Gender and sexual cyber violence and resistance are phenomena that would be difficult to quantify simply because they constitute the diversity of the human experience. (Tenny et al., 2022) states that such behaviours and attitudes, which can be difficult to quantify and capture quantitatively are thus better suited to qualitative research. The research takes on a descriptive nature because ultimately the research paints a picture of how Association Stop Fisha shows gender and sexual cyber violence and resistance on social media and in their book.
In addition, as my research questions were more open ended, making the decision to conduct qualitative research was straightforward (Tenny et al., 2022) and further supported by the considerations in Table 4. It acted as a guiding light in deciding which method to undertake. The decision to conduct a cross-cultural study of Association Stop Fisha and WOUGNET arose from the expectation that the answers to the research questions would not easily be put into numbers (Tenny et al., 2022). Instead it would feature perceptions of the data I collected analysed from social media, book and an interview. Then finally conduct a recognition of themes and patterns which would then be collated into discussions towards the answers.
Table 4. Relevant Situations for Different Research Methods
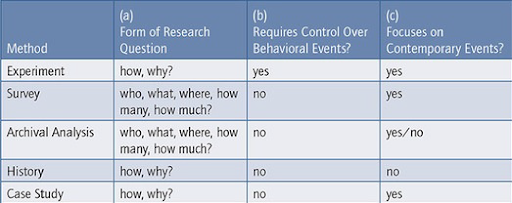
Source: Yin, 2018, p.39
Further pursuant to Table 4, because the research questions were explanatory (featuring “how”), they were more likely to lead to a case study (Yin, 2018). With regards to control over behavioural events, (Yin, 2018) posits that case studies rely heavily on two sources of evidence namely direct observation of the events being studied and interviews of the persons still involved in the events.
In addition to data collected from social media and a book, the case study will include an interview of an employee from the organisation based in Uganda (WOUGNET). I decided on a shorter case study interview which meant the interview took place over one sitting. According to (Yin, 2018), to these types of interviews may remain open ended and take on a conversational manner but follow the interview guide. Therefore, the interview was semi-structured in that it resembled more of a guided conversation rather than a heavily structured query. I prepared 4-6 key guiding questions as shown in Appendix A in order to guide the interviewee in their answer, however I allowed them to add/elaborate to their answer as much as possible in order to gain richer detail for my discussion.
2. Context of the study
First we need to understand the organisations selected for the case study, from their background and how they started, including what they do now in fighting gender and sexual cyberviolence.
2.1 Description of Association Stop Fisha
Association Stop Fisha is an activist collective in France that is made up of 92 students, high school girls, lawyers and employees who have gathered together to fight against gender based and sexual cyber violence in particular the ‘fisha' accounts that exploded in number during the 2020 COVID lockdown. The main hashtag associated with this collective is #StopFisha.
From just a few members to now hundreds of volunteers from all over France, the group continues to raise the alarm about the patriarchy and its resulting violence; whether it is on the street or online. Their commitment is proof of a system failure and the result of an emerging problem; cyber sexism and cyber violence and the resulting sexual and gender bias.
One of the most important things that made Association Stop Fisha stand out was that their inception was during the time of the 2020 COVID lockdown and within two months of existing they had managed to unite more than 12,000 active members ready to help (Stop Fisha, 2023)
Their method of fighting against cyberviolence takes a four pronged approach: the monitoring and reporting of online gender-based violence (track and report fisha accounts), legal and psychological support for victims, raising awareness and finally, advocacy.
2.2 Description of Women of Uganda Network
Woman of Uganda Network (henceforth known as WOUGNET) is a non-governmental organisation that was started in May 2000 by several women's organisations in Uganda to develop the use of information and communication technologies (henceforth known as ICTs) among women as tools to share information and address issues collectively. As an organisation, their vision is an inclusive and just society where women and girls are enabled to use ICTs for sustainable development (WOUGNET, 2023)
Through their mission to promote and support the use of ICTs by women and women organisations in Uganda, they want all women to take advantage of the opportunities presented by ICTs in order to effectively address national and local problems of sustainable development. The new ICTs, in particular, email and the Internet, facilitate communication with each other and the international community. Indeed, access to information about best practices, appropriate technologies, ideas and problems of other groups working on similar concerns have been identified as critical information and communication needs of women organisations in Africa (Women in The World Foundation, 2023)
Although WOUGNET's emphasis is mainly in Internet technologies, they also carry out research in how these technologies can be integrated with more common means of information exchange and dissemination including radio, video, television and print media. As stated before, their vision is inclusivity of women and girls within the context of ICT. Through increasing their capacities and opportunities for exchange, collaboration and information sharing, they aim to improve women's conditions of life.
3. Case study data
3.1 Data collection
I collected three different types of data for the case study namely documents, most notably the book published by the organisation titled Combattre le cybersexisme (Pardo et al., 2021) and social media posts created by StopFisha as well as an interview provided by one employee of WOUGNET. In Table 5, I collated the sources of my data, showing how and when I collected them, their importance and verifiability.
Table 5. Source of data
Method of collection | Time of collection | Importance | Verifiable | |
Documentation (Book) | Online | Dec 2021 | High | High |
Social media posts | Computer assisted | May 2022 | High | Medium |
Interviews | Virtual | May 2023 | High | High |
Source: Author.
The aim was to have multiple sources of evidence used in order to strengthen the reliability of the case study. (Yin, 2018 cited COSMOS Corporation, 1983; Yin et al., 1985) states that one analysis of case study methods found that those case studies using multiple sources of evidence were rated more highly, in terms of their overall quality, than those that relied on only single sources of information. In addition, (Yin, 2018) adds that the need for multiple sources of evidence is greater for case studies than other research methods such as experiments, surveys or histories.
The documents I used (especially the book) allowed a specific, unobtrusive and stable way for me to have direct quotes attributed to the organisation without the interview process (Yin, 2018). Because it is a published piece of evidence, any quotes from it are easily verifiable and it remains accessible both electronically and physically from multiple sources like FNAC and Librarie Decitre. It served as the main source of the organisation's views for all the research questions and thus made a good source for the case study. Although the organisation also had pamphlets, their availability was limited because the access occurred only on occasions I interacted with the organisation in person. Thus they were not included in the data collected.
The social media posts were collected subject to a priori exclusion criteria with specific targets for what they should entail which was expounded upon in the setting and sample section of the methodology.
The biggest difficulty I encountered was with a section of my original plan (to carry out interviews with the Stop Fisha members). As time went on, the possibility for direct interviews was diminished because of the case study deadline. They would have served to make the case study findings in relation to Stop Fisha and conclusions more convincing through what (Yin, 2018 cited Patton, 2015) was known as data triangulation. Although numerous attempts were made to arrange for this source of evidence, unfortunately the organisation was not able to provide time for this.
(Yin, 2018) stated interviews had the potential to yield interesting insights for the case study research due to the difference in opinion between individuals, and in this case the difference between organisations across countries. Luckily enough with WOUGNET, I was able to interview one employee who worked within the organisation.
3.2 Setting and sample
Images from the organisation Stop Fisha's accounts on three social media sites were sampled—Meta, Instagram and Twitter—because two of them are part of the most popular social media sites (Statista, 2022). In addition, the organisation utilises them as part of their social media presence as shown in Image 1 below.
Image 1. Association Stop Fisha's social media presence
Source: AllMyLinks.
(Mumby et al., 2017) stated that the methods chosen for the data analysis has a bearing on how the connections between the different resistance practices and intents (particularly infrapolitics and insubordination) may translate into collective forms of insurrection. Every decision made about the data collection process will thus be justified accordingly.
It is important to first consider that qualitative research tends to use smaller samples than quantitative research, and as such there are no rules for sample size in qualitative inquiry' (Patton, 2002 as cited in Braun and Clarke, 2013). The sample sizes could range from a single participant or text being analysed in depth (e.g. see Crossley, 2007, 2009 as cited in Braun and Clarke, 2013) to a size of 15 to 30 individual interviews to identify patterns across data (e.g. Gough & Conner, 2006; Terry & Braun, 2011a as cited in Braun and Clarke, 2013). For interviews, more than 50 interviews would constitute a large sample in qualitative participant- based research (Sandelowski, 1995 as cited in Braun and Clarke, 2013).
Despite the existing evaluation of the sampling options for periodical media content, the traditional sampling technique is applicable to social media data is largely under-explored (Kim et al., 2018). For this study, purposive sampling was used. This involved selecting data cases (participants, texts, images) on the basis that they would be able to provide ‘information rich' analysis for the study (Patton, 2002 as cited in Braun and Clarke, 2013). This, criteria for the data collection was decided as shown below and the images were downloaded on one day in 2022 for two reasons; to prevent overwhelm because there was only one researcher and because the organisation's data was limited in quantity given the a priori exclusion criteria stipulated for the case study. A priori exclusion criteria were as follows:
- Posts that were reposts/retweets of another organisation's content, because the aim was to understand Association Stop Fisha's data as distinctly separate from other organisations as possible.
- Posts from the year 2021 because the book provided a detailed enough source of data from that time period.
- Posts from individual members of Association Stop Fisha that were featured on any of the pages because the study was investigating the organisation as a whole.
When considering the inclusion criteria, particularly the time period for which to consider for the collection of social media data, the study relied on (Kellogg, 2009 as cited in Mumby et al., 2017)'s assertion that longitudinal and ethnographic methods (Courpasson, 2017a as cited in Mumby et al., 2017) enabled a more thorough understanding of how resistance unfolds over time and space. It was posited that this can provide insights into how micro-political forms of daily oppositional practices might be “scaled up” (Hardy, 2004 as cited in Mumby et al., 2017) to collective forms of struggle (Kelly, 1998 as cited in Mumby et al., 2017) as well as how the thousands of petty acts (Scott, 1990 as cited in (Mumby et al., 2017)) might in themselves result in major change.
The inclusion criteria for social media posts used in the study were as follows:
- Posts on the organisation's social media accounts, not the personal accounts of any of the members of the collective.
- Content shared repeatedly across more than one of aforementioned social media platforms was only counted as once.
- The period of consideration was January 2022 to May 2022.
Thus after consideration of the different factors and criteria considered, a sample of 50 images was collected. As it was not the only source of data for information from the organisation, the sample size was deemed sufficient.
While gathering the images it was important to distinguish between the various months in which they were posted by Association Stop Fisha organisation. Different folders were set up with each month titled accordingly [Month 2022] and the posts from each month collectively downloaded into the respective folders.
When deciding on the data from the book, I again opted for purposive sampling, the a priori exclusion criteria was as follows:
- The consequences of gender and sexual cyber violence as this was not the target of the case study.
- Sections detailing the legal aspects of cyber violence such as ‘The actors of cyberspace regulation' and ‘What the law says' under the different categories of cyber violence because the case study is not an analysis of the law.
- The sections talking about advice for the victims and relatives because it was not the target of the case study.
- Sections from the introduction giving general information on the context and setting.
The sections of the book sampled for the case study were as follows:
- For the sections ‘Introduction', ‘Cyberspace' and ‘Cyber sexism', the purple boxes which contained notes and observations from the organisation.
- Within the section on ‘Gender based and sexual cyber violence', the definitions of the various categories of cyber violence (usually the first two or three pages).
For the organisation WOUGNET, I interviewed one employee virtually in May 2023 as the study is an introductory inquiry into what gender and sexual cyber violence looks like cross culturally.
4. Data analysis
Because the images I gathered and the book needed to be analysed simultaneously, I decided to utilise Computer Assisted Qualitative Analysis Software (CAQDAS) for the coding. There are numerous choices on the market with many covering both text and video-based data (Yin, 2018) such as Atlas.ti, Nvivo, Delve and HyperRESEARCH. For this analysis, the aim was a high level of analysis with ease of use, reasonably priced and a short learning curve. I used Dedoose (as shown in Image 2) to analyse both the images and textual data because it fulfilled those requirements.
Image 2. Dedoose Software Interface
Source: Dedoose Software 9.0.54.
Despite the ease and quickness of these tools, they are still just tools meant to reliably assist in creating outputs such as the occurrence of words or codes (Yin, 2018) and conduct searches for multiple combinations of codes in the data. Armed with the knowledge that the outputs were not the final step of my analysis (Yin, 2018), my direction for data analysis took one direction; thematic analysis.
Thematic analysis is a method for identifying, analysing and reporting patterns (themes) within data. It minimally organizes and describes the data set in (rich) detail. However, frequently it goes further than this, and interprets various aspects of the research topic (Boyatzis, 1998 as cited in Braun and Clarke, 2006).
After collecting the images from social media and reading the book, I used the research questions as the jumping point for decisions on data analysis. Data analysis followed the phases as depicted in Table 6(Braun and Clarke, 2006)(Braun and Clarke, 2006).
Table 6. Phases of thematic analysis

Source:(Braun and Clarke, 2006), p. 87
For the first phase, as a way to get started with familiarizing myself with the data, I took copious notes both by hand and within the data set itself. Using memos (as pictured in Image 3),
Image 3. Memos taken while familiarising myself with the data
Source: Author using Dedoose Software 9.0.54.
This was the beginning of my analysis building as I wanted to remember what initial ideas I had when I started generating my initial codes for the second phase. These memos also served as hints, clues and suggestions for ways to interpret the data and connect the ideas I would end up having later on (Yin, 2018). While continuously reviewing the data from the social media and book, I occasionally noted descriptions however I did not do this strictly throughout the entire process as I knew I would consolidate the codes into themes during phase 4.
Reaching the second phase, my coding strategy was to start with the images then move onto the book and code the samples specified in 3.2. This process yielded a total of 72 codes (11 parent codes and 61 sub codes) which I proceeded to check recode for phase 4.
Phase 5 involved exporting the codes into a word document to compare the golden threads running through the various codes. I consolidated the most similar sub codes and continued to refine my themes to end up with 3 big themes with 12 sub codes. From this I was able to reduce the themes down to one theme.
For the interview data, I also used the process of thematic analysis as it as the most straightforward and time conscious method for the case study.
4.1 Ethical considerations
I had planned to interview members of the organisation after informally meeting a selection of them at 24H contre les violences sexists et sexuelles, a 2 day conference held by Theatre Des Célestins in Lyon in November 2021. Though I reached out in February and again in April to schedule the interviews, I was unsuccessful so I worked with only data collected for the case study instead i.e. images from social media and the book written by the organisation.
Meta and Instagram's copyright policies only allow the ability to post content as long as it does not violate someone else's intellectual property rights (Instagram Help Center, no date). Therefore, as I only needed the images for my own private use in education I did not need to repost or re share them on any social media.
(The European Union Intellectual Property Observatory, 2022) notes that it is possible to download a copy of a work from the internet, in accordance with the private copying exception, such as private use if the source of the copy is lawful. In addition, the downloaded copy must not be shared afterwards. In keeping with the appropriate copyright restrictions, I will not reproduce the images used in the analyses presented here. The images can be found on the organization's social media platforms with Meta, Instagram and Twitter under the user name @StopFisha as seen in Image 1.
The book (Pardo et al., 2021) titled Combattre le cybersexisme, was purchased with my own means, and again in accordance with the (The European Union Intellectual Property Observatory, 2022) I limited my analysis as described in Part 3.2 and quotations of the book for only specific purposes i.e. educational with the source of work and author names always mentioned.
4.2 Limitations
It was more difficult to find data meeting the a priori exclusion criteria on Twitter, than on the other two social media sites Meta and Instagram. This could be because of Twitter's interaction model being more conversational i.e. responding to other tweets and retweeting can make up the bulk of an account's interactions. As such, majority of the organization's data from Twitter was excluded because it was mainly interactions amplifying or commenting on other organisations' content not original tweets fulfilling the criteria.
The CAQDAS software used (Dedoose) while easy to intuit and begin using was not useable while offline. Because the data was inaccessible without the internet, it is not recommended to researchers with irregular internet access.
5. Presentation of results (Stop Fisha)
From my analysis of the data from Stop Fisha I made a number of observations. The first was that while the case study aimed to treat the book and social media data as one data set, there was a difference in the portrayal of cyber violence depending on the data source. In the book, there was an increase in detail of description of the various cyber violence. This was expected because the use of social media limits verbosity i.e. limits in Twitter characters to 280, max 10 Instagram images for a post.
The overlap of cyber violence was incredibly prevalent i.e. some types of cyber violence involved the other for example; pedocrime usually begins with grooming, sextortion can result from the doxing and dissemination of intimate content and hacking can lead to identity theft and catfishing.
During the data analysis, I used Dedoose to generate a word cloud that is pictured below. It is useful to understand the how the different codes and sub codes were eventually refined into two themes by providing the big picture of those codes.
Image 4. Word cloud generated during the analysis

Source: Author using Dedoose Software 9.0.54.
The theme I was able to deduce from the book and social media data was a victim focused approach interspersed throughout the Association Stop Fisha's communications (social media and book).
In their data, Association Stop Fisha sometimes reflects in a positive light by showing a desire through empowerment and inclusivity to the victims but also by trying to shed a truthful light on not only their victims but those around them that are affected by the gender and cyber violence experienced. While breaking down the definitions of the different types of cyberviolence, Association Stop Fisha used a mixture of elements including the background of the cyberviolence which could be related to its meaning or origin, the actor of the cyberviolence and details of how the act takes place/ is enacted.
Furthermore, their data showed that there is a now an equalization between real life and cyber space in terms of the effects of the actions on cyberspace and the severity of the activities that happen. Some of the effects experienced by women included but we not limited to, damaged reputation, dispossession of image and body, limited access, loss of means, loss of privacy, physical harm, psychological side effects and death.
We also see that in understanding these effects there comes to be an equalization between real life and cyber space in terms of the effects of the actions on cyberspace and the severity of the activities that happen.
6. Presentation of results (WOUGNET)
WOUGNET's data was provided from an interview conducted with an Assistant Technical Support Officer. She works as a digital literacy and security trainer for the organisation and has also led various projects for the organisation to end online harassment among women journalists.
According to her, the most common types of online gender based violence they encounter among women in Uganda are online stalking, non-consensual distribution of intimate images, online grooming, doxing and trolling. She also mentioned a prevalence in these kinds of attacks being more frequent among women in the urban areas as opposed to rural areas. She added that it was due to those in urban areas having easier access to technology and mobile phones. For the purposes of this study, urban areas are considered the major cities all over Uganda such as Kampala, Jinja, Mbarara, Kabale, Fort Portal, Mbale.
In terms of activities carried out by WOUGNET against gender and sexual cyberviolence, there were two main activities namely research, advocacy and awareness raising, capacity building and policy engagement. She mentioned their online and in person campaigns that they carried out to share information about online gender based violence where the aim was educate the community on the different types of online gender based violence and their impacts to the people who experienced them. Some of these online campaigns took place over social media and others were in person through engagements across schools. Through the use of art, tech pop ups, the organisation continues to spread knowledge on online gender based violence to girls and young women. Their advocacy included creating a toll free line for the victims to call and report their experiences, ask questions and be connected to the necessary authorities when necessary.
The capacity building was a two pronged approach; first teaching women to use the digital technology and then later on teaching them how to be safe online especially in areas where the knowledge of digital technologies is not as prevalent. For policy engagement, this involved meeting with different stakeholders such as law enforcement and law makers to bring about high level discussions on online gender based violence.
Part 3: Discussion
Introduction
The case study's objective was to understand how gender and sexual cyber violence are portrayed, and the activities the organisations use to tackle cyberviolence within the context of resistance. The discussion will explore the answers to these questions from the point of view of each organisation through the themes generated from the findings respectively, then a discussion of the resistance context of each along with recommendations for the problem along with the conclusion.
1. Association Stop Fisha
1.1 How is Association Stop Fisha portraying cyberviolence?
From a thematic analysis of Association Stop Fisha's social media and book data, we start to understand the picture that this organisation paints in relation to cyber violence. Overall, their communications harbour a focus on the victims of cyberviolence whether by highlighting positively through empowering them and being inclusive or employing fact based personalization. Throughout both of these ways, we can see the equalization of cyberspace and real life because the effects of these violence within the cyberspace spill over to affect women's lives offline.
An example is the quote below which although does not use the word victim, it brings to the forefront of mind what kind of effects the cyberviolence at hand has on the person experiencing it.
“The person whose identity has been usurped: the perpetrator of the offense can harm their image, their tranquillity and their well-being, this is particularly the case when the usurper creates an account in the name of the victim on a porn website. » (Pardo et al., 2022, p. 156).
This excerpt is in relation to the act of identity theft. It goes even further by saying:
“The person who is deceived by the use of the false identity: by pretending to be another person, the usurper will often scam a third person, by extracting information or money from them. This technique is used in particular by child criminals to approach their victims. » (Pardo et al., 2022, p. 156).
These excerpts in relation to identity theft make it clear that the victims who experience this kind of cyberviolence can fall into different categories, either having their identity stolen or by being deceived by a perpetrator and in either situation, it is made clear that the occurrences are not the fault of the victims. This kind of language is helpful in shifting victims' perception of themselves after experiencing the kinds of variations that can occur in a situation as common as identity theft. In this way, we see that the book Combattre le cybersexisme is not only an information guide but another way that Association Stop Fisha works to offset the effects of gender and sexual cyberviolence and the victim blaming that usually arises from violence in general.
With the definitions of the different gender and sexual cyberviolence terms, the book breaks these down into three parts namely the background of the term where applicable, the actors who perpetrate the cyberviolence and how it occurs. This kind of breakdown is shown in the table;
Table 7. A breakdown of acts of cyberviolence in Stop Fisha's Combattre le cybersexisme
Term | Background of the words | Actors of the violence | How the act occurs? |
Blackmail on cam | Blackmail that occurs on camera/ through the use of technological devices | A man pretends to be a woman in order to trick another man and steal sexual content from him and then blackmail him. People who use this technique are called grazers. | Another cam blackmail technique is to create a fake virtual profile2 and get in touch with anyone on the internet, often through a dating website. As the exchanges escalate, the aggressor invites the victim to continue with a more intimate video conversation and will record their textual and visual exchanges without the consent of the person concerned. |
Catfishing | n/a | Someone hides their identity by pretending to be a friend, a classmate, a possible lover or even a fictitious character | Done in order to facilitate a relationship. It usually happens a lot with grooming. |
Cum tribute | An English word that translates to “sperm” and the term tribute means “homage”. | The person takes pleasure in photographing the result: the photo of the person covered in sperm. | The act of masturbating and ejaculating in someone's photo. |
Cock tribute | Cock is an English word that means “penis”. | The perpetrator takes a photo of his penis – often erect – next to someone's photo. | This photo will then be disseminated and sometimes sent to the person who appears in it. |
Creepshot | In English, shot means “cliché” or “photo” and the derogatory word creep means “dirty guy” or “weird guy”. | Someone takes the photo without consent. | This photo could be taken while they are walking down the street or lying on a beach, for example. |
Cyberbullying | A form of harassment carried out electronically including by telephone, email and social networks | An individual or group of individuals | Cyberbullying can take several forms: the multiplication of phone calls or written messages or even flaming |
Cyber outing | Forced outing or coming out is the act of revealing the sexual orientation (lesbianism, homosexuality, bisexuality, asexuality, etc) and/or gender identity (non-binary, trans identity, intersex, etc.) of a person without their consent | outing by a person from the LGBTQIA+8 community; and outing by someone who is not one of them and who is, in most cases, LGBTQIA+-phobia. | Such information can thus be communicated to their relatives, to their employer, in the newspapers, and/or on cyberspace. |
Deep fake | The result of the contraction of the words deep learning and fake. | A successful montage is claimed as a “masterpiece” by its creator, but for the victim, it is a nightmare | A montage made from a photo, video or recording, which has the particularity of being so successful that you do not realize that the image is faked. |
Deep porn | A form of sexual deep fake | An anonymous creator/group | Taking a person's face and replacing their body with that of a naked body that is not their own. The montage is then massively disseminated on the Internet. |
Dick pics | An English expression that literally means “penis photo”. | Can be anonymous or known to the victim | Sending a photo of a penis to a person without their consent therefore imposing the image on the sight of the recipient without giving them the choice to see it or not. |
Doxxing | an English term designating the disclosure of personal data on the Internet relating to the private life of a person with the aim of harming them | individual | This may include revealing where they live, work or study, and may go as far as leaking their banking information, for example. |
Flaming | n/a | In the vast majority of cases a “proximity violence”. Thus, the victim often knows their perpetrator, the latter may be a classmate or a student from the same school. | Refer to trolling and cyber bullying |
Fisha account | An account called “fisha”, verlan of the term “poster”, is an account or a group created on a social network, a platform or a messaging system. Fisha accounts often bear the name of cities, departments or neighbourhoods in order to list and centralize the victims and to be able to identify them more easily. They are called: “fisha78”, “affichepute_rouen”, “salopedu95”, etc. | By calling themselves “judges”, the “fishers” (those who manage the fisha accounts) and viewers sanction the victims by taking them to court in the public cyberplace. | The content published without the victim's consent is often accompanied by their personal information such as their name, their first name, their identifiers on social networks, their telephone number, their school's name or their address. Concretely, the victims' content is shared and re-shared. |
Grooming | n/a | By discussing with the victim, the pedophile can choose to assume his identity with her. He can also hide his identity by pretending to be a friend, a classmate, a possible lover or even a fictitious character in order to facilitate grooming: this is what is called catfishing. | We speak of grooming when a pedophile targets his victim and discusses with her in order to build a friendly and/or romantic relationship and thus, to create an emotional connection with the aim of coaxing them and persuading them to have physical or virtual sexual relations with him (examples: sexting, sending intimate images or videos, sexual blackmail and/or threats). |
Hacking | n/a | The actor does so in order to take control of it or to access a person's personal information and data and then to exploit it. | A set of computer manipulations make it possible to enter a computer system (telephones, computers, etc.) |
Happy slapping/ video lynching/ video aggression | In English, this expression literally means “to slap happily” and it is a pun on the expression “slap happy” which refers to a cheerful and good-natured attitude. | The person does so with the aim of inflicting even more humiliation on the victim. | A practice that consists of filming a physical or sexual assault and disseminating the images |
Identity theft impersonation | The use of another person's identity without their knowledge | Without the consent of the victim, the actor will use personal information that allows them to be identified e.g.name, telephone number, date of birth, address, photographs, etc. | Identity theft usually begins with the collection of personal information about the victim. It happens that acts of identity theft follow acts of piracy or hacking. However, identity theft can also occur as a result of forgetting to log out or sharing a password with a friend or boyfriend. |
Incitement to rape | On social networks, feminist activists bear the brunt of this on a daily basis. The purpose is to try maintain a form of domination over them and silence them | An individual | This is when an individual encourages others to rape a specific person. |
Leaked content from online sex workers | Cyber-sex workers use the Internet to sell erotic and/or sometimes pornographic content (ranging from nudes to personalized images and videos, responses to specific queries or intimate videos, etc..) via websites created for this purpose such as Only Fans | Anonymous individual or user known to them | Theft of information or (immaterial) goods. |
Pedocriminality | “Pedophilia” comes from the Greek pais, pados which means “child” and philein which means “to love with friendship”. “Pedophilia” therefore literally means “one who loves children” and is therefore an inappropriate term to describe criminally reprehensible acts. | An older person who can be anonymous or known to the child. | Thus, in practice, “this sexual violence is facilitated by digital tools” which become real points of contact between the adult and the child. |
Revenge porn/ sharing intimate content | The term “revenge porn”, which literally means “revenge porn”, refers to the particular case of an ex who, after a breakup, disseminates sexual content from their former partner. | Refers to the particular case of an ex who, after a breakup, disseminates sexual content shared privately from their former partner | This act can also be the result of a whole variety of schemes which are excluded from this definition, and in particular hacking, stolen photos or even creep shots. |
Sextorsion | A mix of the words, sex and extortion | The cyber aggressor may be known to the victim (classmate, boyfriend or ex, work colleague, neighbour) as he may be unknown to them. | If the aggressor is not physically present, he is dematerialized, behind his screen. The victim is also behind their screen and in front of their camera, which becomes both the eye and the weapon of the executioner. Pressure is exerted on the victim to perform obscene acts of a sexual nature in front of the camera of their computer or telephone This pressure consists of threat of disclosure of images or doxxing |
Trolling | The term troll refers to the monstrous elves of the countries of the North reputed to be dangerous. Shitstorm is a neologism was created by the media to designate the phenomenon of the unleashing of virulent criticism towards a person, a group of people or even a company on the comments of websites, blogs or social networks. | They parasitize an online community by constantly posting messages aimed at denigrating it. These aggressive Internet users also like to generate controversy and often attack other Internet users | Can take the form of dogpiling where a large number of accounts (and therefore Internet users) simultaneously fill the comment thread of a post with criticisms and/or insults aimed at a specific person. These comments may also be accompanied by the sending of private messages. |
Upskirting | Up skirt literally means “under the skirt” | Involves someone taking photos without consent | The practice of taking photographs under a person's skirt or dress, thus capturing an image of their crotch and therefore, their underwear and sometimes their private parts, without their consent. Sometimes the person being photographed doesn't even realize it. Often, these photos target people perceived as women, and, more specifically, their buttocks, their legs or their low-cut. |
Source: Author.
Because of the wide variety of gender and sexual cyberviolence acts described within the book, use of the framework provided by (Backe et al., 2018) in Table 1 would not be sufficient. The book, being written in 2021 has expanded upon the various cyberviolence tactics so the aforementioned framework would not provide a sufficient look at the different types included within. This kind of framework works to encapsulate a larger number of types of cyberviolence but also provide a clear description of what the perpetrator's actions and identity may look like in order for them to be easily identified by those experiencing cyberviolence.
In relation to fact based personalization present throughout their book and social media, we see a combination of various factual elements such as statistics and figures with real life cases that achieves various effects like personalizing the violence.
An example is this quote about the founder of Bumble who experienced violence at the hands of her then intimate partner, Justin Mateen. Though they founded the dating app Tinder together, she left 2 years later and founded Bumble. This is a real life case of violence mentioned in the book
“What's special about Bumble, which like Tinder is a dating app, is that it empowers women to make the first move and, thus, puts them in control”, (Pardo et al., 2022, p. 17).
This quote highlights a story of abuse experienced by Whitney Wolfe Herd at the hands of her then boyfriend. Alone, it can be seen as just a random fact but within the context of the book, it shows a very deliberate effort on the organisation's part to putting faces to the women who experience cyberviolence.
Another real life case of women experiencing cyberviolence detailed within the book is the French influencer Louise Aubery, @mybetterself, who was mentioned as suffering from dogpiling in particular during her action to fight menstrual poverty in December 2020. This framing of the definition of the gender and sexual cybercrime has the potential to be more effective towards a wider audience (both men and women) especially when one considers the usual refrain of “I have a sister/wife/girlfriend” from men when confronted with the possibility that their behaviour may be abusive.
We can see this further with the “mighty girl” effect, a term coined by (Borrell-Porta, Costa-Font and Philipp, 2019) in their study where found that men with daughters hold less traditional views on gender roles. They added that this study's results were in line with the notion that the more contact men have with their own daughters, and the more that their daughters have contact with the outside world, the more that men want women overall to be able to be independent and self-sufficient should they choose to be.
It is important to also note that the study was conducted within the United Kingdom and this may not account for cultural differences present in France. A study of the same could potentially be conducted in France, maybe observing the men's attitudes over time.
While it does not preclude these same men from being abusive, it serves as a window into aligning their frame of mind towards the women in their own life. In this way, the portrayal of gender and sexual cyber violence within Association Stop Fisha's book and social media can be seen as subversive in its approach to framing of gender and sexual cyberviolence.
Within fact based personalization, we see the organisation's approach is very deliberate in putting faces to the women who experience cyberviolence. Their social media is no different in that regard. Through the use of an image of as shown below, the audience gets a look at the faces of the victims of cyberviolence.
Image 5. Social media post about a victim of deepfake

Source: Association Stop Fisha
In this case, the victim was named Basant Khaled and she was a victim of deepfake/deep porn after rejecting the sexual advances of two boys in her class. Her image is included in the post to make viewers and its effect is that we see how undeniably young she is, which makes a viewer in turn think of the women in their own life possibly experiencing this same type of cyberviolence. Another element of this personalization is the inclusion of Basant Khaled's last words to her mother before she committed suicide as shown in the image.
Image 6. Basant Khaled's last words to her mother

Source: Association Stop Fisha
In the extract from the last letter she left to her mother, she writes,
“Mom you have to believe me, I'm not this girl. These images were photo shopped, I promise! I don't deserve what's happened to me. I'm suffocating, I'm tired”, (Khaled, 2022) As mentioned in the literature review, an individual who has experienced sexual violence experiences it as a public and private harm because of the shame and taboo associated with it. In this instance, the public nature of the cyberviolence, the video being disseminated to all her classmates highlights how women's experience of sexual violence have become more public in the digital age.
In addition, this social media post shows one of the more devastating effects of gender and sexual cyberviolence, death. It affirms the equalization of the cyberspace and real life, in that the happenings online do not just remain there. They can spill over into real life with devastating effects on victims who have experienced abuse and their families.
Another case of equalization of cyberspace and real life is how psychological and physiological effects can be experienced despite the instance of cyberviolence happening within the cyberspace. Association Stop Fisha highlights this through a social media post about an article as shown in the image as shown in the image.
Image 7. Psychological and physiological effects of cyberviolence in the metaverse

Source: Association Stop Fisha.
From being the victim of constant cyber harassment attacks from other male avatars, her reaction to this cyber harassment experienced online spilled over into her real life. These attacks rendered her frozen which in turn will affect her navigation of the cyberspace going forward.
With regards to the use of statistics within the book, the effect of Association Stop Fisha's utilisation is a sobering reminder about the pervasive nature of the gender and sexual cyberviolence. For example, these quote about happy slapping, grooming and doxxing.
“According to the e-Enfance (e-childhood) association, happy slapping affects young people between the ages of 11 and 17 in 90% of cases, both girls (45%) and boys (55%)”, (Pardo et al., 2022, p. 129).
Happy slapping is shown to start from a very young age in the statistics presented within the quote. It is a reminder that adults are not the only perpetrators of these types of cyberviolence.
The quote on grooming, shows how much incidents of grooming increased but also how easily it can happen to one's child through social media such as Tik Tok and Instagram which are major targets. But even without social media, grooming can still occur on online video games for children and young adults such as those mentioned within the quote below.
“According to a survey conducted in January 2019 by the NSPCC (National Society for the Prevention of Cruelty to Children): ➜ Grooming is mainly done on social networks such as Facebook, Messenger, Snapchat, Discord, but especially TikTok and Instagram (where grooming has increased by 200% from 2017 to 2018)1. ➜ This practice is also found in online video games for children and young adults such as OhMyDollz, Plato and MovieStarPlanet”, (Pardo et al., 2022, p. 125).
On their social media, Association Stop Fisha utilises statistics in a different way. Instead they use it to raise awareness, for example about the importance of 8th of March (International Women's Day) is as shown in the image below.
Image 8. Social media post with statistics about violence women face
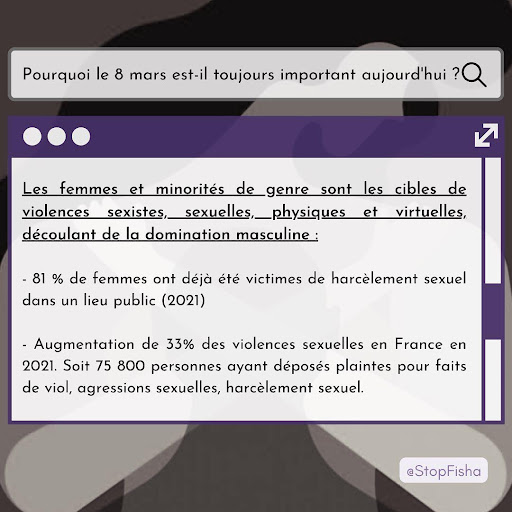
Source: Association Stop Fisha.
This specific post provides the context of violence experienced by women and a sobering reminder that despite it being Women's Day, the state of being for sexual and gendered minorities is not at its best and can stand to improve. Regardless of Women's Day celebrations, the literature has shown that patriarchy's effects are widespread and the statistics pictured highlight this even further.
1.2 What activities is Association Stop Fisha undertaking in the fight against cyberviolence?
The activities Association Stop Fisha undertook in the fight against cyberviolence range from providing legal recourse for those who have experienced cyberviolence, creating conversations and safe spaces, sharing information about cyberviolence and its effects and protesting.
The first activity that Association Stop Fisha undertakes in the fight against cyberviolence is the sharing and dissemination of information through their book Combattre le cybersexisme which was written as a guide for all to learn about gender and sexual cyberviolence. It is quite comprehensive in its nature, providing statistics, real life cases and examples of women who have experienced cyberviolence and even legal knowledge on the laws in place to protect women in France.
The second activity Association Stop Fisha engages in is creating conversations. On their social media, Association Stop Fisha routinely engages with their audience and interested parties by inviting them to share on relevant topics such as creating a safer internet space as shown in the image below:
Image 9. A social media post that will create conversations

Source: Association Stop Fisha.
This post highlights the key work of Association Stop Fisha in reversing the silence surrounding victimisation when experiencing gender and sexual cyberviolence. This serves as an opportunity for women to engage in what is known as technofeminism. According to (Wajcman, 2004), technofeminisms conceive of a two-way mutually shaping relationship between gender and technology in which technology is both a source and consequence of gender relations and vice versa.
Through encouragement of the sharing of ideas, Association Stop Fisha embodies (Wajcman, 2004)'s idea that analyses of technology must include a technofeminist awareness of the differential positioning of women and men as designers, manufacturers, salespersons, purchasers, profiteers and embodied users of technologies.
In relation to resistance, this activity is of a post structural nature in that it focuses on the discursive nature of challenging the meaning of what a safe Internet means. The audience is invited to contest the meaning of what it means for the Internet to be safe i.e. is it an Internet without men, a separate Internet for men and women, and other kinds of ideas. Despite this, I would argue that Association Stop Fisha should be categorized as an organisation that embodies structural framework because their organisation began as women uniting around a common pain in the middle of the pandemic. It is an organizations that shows time and time again that it values the feminine especially considering its approach in portrayal of victims.
The third activity is the execution of collaborative efforts undertaken by Association Stop Fisha in fighting gender and sexual cyberviolence. One of their collaborations is evidenced by the social media post of image below. It shows that the organisation is in collaboration with e- Enfance. E-Enfance is an organisation that works towards the protection of children on the internet.
Image 10. Association Stop Fisha collaborates with other organisations

Source: Association Stop Fisha.
It lends legitimacy to Association Stop Fisha's activities to partner with them and demonstrates resistance within the structural perspective because again they are showing the Advocacy and work to raise awareness of cyberviolence is a direct example of this consciousness-raising.
The fourth kind of activity carried out by Association Stop Fisha is protest actions such as the one shown in the image. (Powell and Henry, 2017) states that as the existence of a multitude of diverse examples of technology-facilitated sexual violence show, the law has struggled to evolve equally in pace with the technology. Therefore, many jurisdictions are yet to decide whether to introduce new legislation to tackle new types of cyberviolence as and when they emerge.
The image shows the participation of the organisation in calling for the inclusion of gendered cyberviolence in the Digital Services Act, which is the legislation regulating the cyberspace at the European Level. This kind of activity speaks to the organisation's attempt to transform one of the main forces that maintain systemic hierarchies of gender as applied to the framework by (Thomas and Davies, 2005). Therefore, Association Stop Fisha's activity is within the structural feminist perspective.
Image 11. Social media post showing protest action by Association Stop Fisha
Source: Association Stop Fisha
However, (Powell and Henry, 2017) emphasizes that despite the importance of the law in mitigating the effects of gender and sexual cyberviolence, there is still a challenge when designing new legislation that accurately and concisely captures the harm while providing sufficient methods of redress to the victims. In addition the law may also contribute further to harms through victim blaming. This makes it clear that Association Stop Fisha's activities are all of equal importance and stand to be more effective when they are utilised together.
Creating safe spaces through festivals shown in the image below, show Association Stop Fisha's efforts in alleviating the silence and shame brought about by experiencing sexual violence. These kinds of spaces are where women are allowed to share freely about their experiences of sexual and cyber violence, ask questions and seek guidance about their lived experiences.
Image 12. A poster for the Woke-end Festival

Source: Association Stop Fisha
To understand the resistance context of this activity, we can apply the (Thomas and Davies, 2005) framework in the recognition of the resisting subject as existing within the structural feminist perspective. As stated before, Association Stop Fisha is an organisation features women united around a common pain and it is also a new kind of organisation that values the feminine especially in their experiences of gender and sexual cyberviolence. Ultimately, these kinds of gatherings are meant to champion women's rights.
(Fraser, 2007, 2009 as seen in Powell and Henry, 2017) notes that the capacity to narrate one's experience of sexual victimisation online, and to share this with a community of one's peers, can be interpreted as an individual and collective act that seeks to correct the injustices of gender misrecognition. In participating in this festival, Association Stop Fisha embodies both individual and collective acts in trying to correct cyber violence. Individually, through each of the members but also collectively in their participation as an organisation in community with other organisations working for women's freedoms.
2. WOUGNET
2.1 How is WOUGNET portraying gender and sexual cyberviolence?
From a thematic analysis of the interview conducted with a member of the organisation, the theme that emerged to answer this question is skills and knowledge based gaps. In contrast to the French organisation Stop Fisha, WOUGNET showed that there was an existing knowledge and skills gap in regards to gender and sexual cyberviolence. This knowledge gap existed in both the women who experienced the cyberviolence and the stakeholders the organisation would interact with to fight against cyberviolence.
2.1.1 Knowledge gaps among the women experiencing cyberviolence
The first and most important knowledge gap present with the women who experience cyberviolence is the understanding that what they are experiencing is gender and sexual cyberviolence. Esther said,
“…from the research we conducted, we realized that some of the women and girls in the community at large do not actually know that they are facing online gender based violence”, (Nyapendi, 2023, p. 6).
This shows that some of the women do not understand these experiences that they sometimes have online are not right. WOUGNET's aim is to impart the knowledge of gender and sexual cyberviolence to as many women as possible, so that they are not confused when violations are happening.
An existing trend Esther mentioned is that the women in urban areas experience more attacks of gender and sexual cyberviolence because they have easier access to technology such as smartphones and computers. However, in the instances where the women in the rural areas experienced online gender based violence, they did not know that it was a type of violence that they should even report. A report by (WOUGNET et al., 2016) confirmed that only 18% of Ugandans live in urban areas with a majority of Ugandan women living in rural areas. This further highlights their vulnerability and limited access to information in dealing with cyberviolence.
To go even further, we see a recurrence of a similar theme from Association Stop Fisha about the equalization of real life and cyber space when Esther says that the women then only feel pushed to report when there is an escalation,
“…they just ignore it until it really escalates to the high levels, that's when they kind of inquisitive to what is happening and how they can ask for help and all that”,(Nyapendi, 2023, p. 6).
An example of an escalation is online harassment transitioning to offline harassment. She brought up a scenario of how someone can be cyberstalked and the lack of response or blocking them can cause the perpetrator to follow the person offline. Toxic masculinity is the idea that our society's definition of manhood is inseparable from the oppression of women (Samuel, 2017). Similarly to a man chasing you down when you refuse to give him your attention, women have to consider and weigh the spill over effects they may encounter offline if they ignore or block an unwelcome comment within the online space. This kind of behaviour online only serves to show how deep the patriarchy's reach is within online spaces when men feel entitled to access to women's attention and bodies even online.
The second knowledge gap present with the women experiencing cyberviolence is confusion between the types of cyberviolence,
“A scenario that regularly occurred is some of the women didn't know how to differentiate between which type of online violence they were experiencing”, (Nyapendi, 2023, p. 6).
From this we can see that the women may not be able to know which of the different types of cyberviolence they are experiencing. This in turn makes it difficult for them to seek help from the law enforcement authorities as they have to know what crime they are reporting. During the interview, Esther mentioned the gender and sexual cyberviolence types that were deemed most commonly experienced by women in Uganda included; online stalking, non-consensual distribution of images, online grooming, cyberbullying, trolling and doxing. (Backe et al., 2018) acknowledged the lack of consensus within the research community on how to define and categorize these behaviours and actions, so it is not surprising that even the victims find themselves confused the differences between them. From the literature reviewed earlier (Table 1), we can further confirm the definitions of the gender and sexual cyberviolence Esther refers to by comparing them to the tactics featured.
Trolling is described in relation to the victim as shown below;
“…an activity that someone hashtags your name…a lady that we interviewed, talked about how her pictures were linked on Twitter and she was being hash tagged”, (Nyapendi, 2023, p. 3).
Although, this description does not match the tactics featured in Table 1, it also touches on the non-consensual distribution of images by touching on the Linking of images on a social media network in a way that was not intended by the person in the image.
Another type of gender and sexual cyberviolence that was defined in relation to the victim was online grooming. This was explained as tricks or pressure that women face or are tricked into sexual activities. A more elaborate description also further relates the same type to non-consensual distribution of images by mentioning the solicitation of naked images and non-consensual sharing of images with the aim to intimidate the receiver.
However, there are the definition that match the tactics described in the table. For example the definition of impersonation as when someone creates an account and shares information or bullies another person. The table describes the tactic of impersonation as creating an account using the name or the domain name of another person, often with the intent to harm, harass, intimidate, or threaten others. The definition provided by Esther matches, although it may not be as broad as the description in the table. The non-uniformity of cyberviolence definitions contributes to the legal blur caused by law makers, which in turn makes law enforcers less likely to help and to hold perpetrators accountable.
2.1.2 Knowledge gaps among the stakeholders
The knowledge gaps present among stakeholders exist among lawmakers and law enforcers who are both important stakeholders in the fight against gender and sexual cyberviolence. To begin with, the first knowledge gap exists knowledge that online violence is violence and that the perpetrators should be punished. As the people the violence is being reported to, Esther also briefly mentioned that the law enforcers are limited in their knowledge on how to pursue some of the perpetrators particularly in the instances of crimes like impersonation where someone creates an account and shares information or bullies another.
The second knowledge gap among the stakeholders exists with law enforcers who do not understand the difference between the different types.
“That is also a challenge when they report to the police and the police cannot help in that matter because if someone comes and says, ‘I'm facing online harassment', and yet it's cyberbullying, then the police cannot be able to help specifically to solve that matter”, (Nyapendi, 2023, p. 3).
The Table 2 further shows justifies the importance of this distinction because both cyberbullying and online harassment are mentioned along with their related terminology. However that these two terms are not to be used interchangeably for each other. From this it becomes even clearer as to the importance of law enforcers knowing the different types of gender and sexual cyberviolence. In order to enforce the laws in existence against the different types, they too must know the different terminology, which is why WOUGNET works to fill those gaps with them.
The second knowledge gap among the stakeholders exists with the lawmakers regarding the laws they put in place to fight gender and sexual cyberviolence. Esther mentions the ambiguity and broadness of the laws in place such as the Computer Misuse Act 2 of 2011 (hereafter referred to as the Computer Misuse Act). She adds that it does not specify the different types of cyberviolence as below,
“The Computer Misuse Act does not specifically look at online violence or cyber stalking so that becomes a challenge when victims report to the police and they do not have a direct way to help them because the law then does not look at specific types of violence”, (Nyapendi, 2023, p. 4).
The Anti-Pornography Act 1 of 2014 (thereafter referred to as the Anti-Pornography Act) though it has had key sections declared unconstitutional by the Constitutional Court (Goitom, 2021) is still a key legislation when it comes to gender and sexual cyberviolence. However, it exhibits a victim blaming approach.
“…when someone posts for instance, my intimate images, I am the one being affected. The law does not actually look for the one that posted them, but I am being affected”, (Nyapendi, 2023, p. 6).
Overall, both lawmakers and law enforcers need to understand and empathise with the rippling effects of gender and sexual cyberviolence on the online and offline lives of women who experience it. Gender and sexual cyberviolence can be experienced by anyone from any social class or tribe or occupation. Esther mentions multiple of women in the Ugandan public eye who have experienced the effects of gender and sexual cyberviolence such as Desire Luzinda, Judith Heard and Lynda Ddane who both experienced non-consensual distribution of images. Their occupations are singing, modelling and television presenting respectively.
In 2014, after a disgruntled ex-boyfriend leaked her pictures, the Ugandan ethics minister at the time called for her arrest, stating that she should be locked up and isolated (Sullivan, 2021). His statement is an example of how normalised a victim blaming approach employed by both lawmakers and law enforcers when it comes to treatment of gender and sexual cyberviolence in Uganda. Victim blaming is defined as a range of direct and subtle ways in which the victims of sexual violence and harassment are blamed for their experiences (Samuel, 2017). Esther further mentions that victims seeking redress through reporting gender and sexual cyberviolence to law enforcement are likely to be asked questions as below,
“What were you doing online? Why did you post that image?”, (Nyapendi, 2023, p. 5).
This not only shows the victim blaming approach, but does nothing to aid the fight against gender and sexual cyberviolence. Instead, it amplifies rape culture and keeps the power structures of the patriarchy in place further continuing the instances of cyberviolence.
In addition it speaks to the censorship of women's actions online that exists as an extension of the patriarchy. Further censorship can be gleaned from statements referencing the 2021 election shutdown of Facebook in Uganda.
“Once you face online harassment and violence on that platform, you cannot be helped, because the question is, ‘It was blocked in Uganda, what were you doing there?'”,(Nyapendi, 2023, p. 6).
In reference to the laws in place we see that both the Anti-Pornography Act and the Computer Misuse Act are rooted in the conservative values that Uganda is known for as a country. For example the Computer Misuse Act only looks at regulation of technological devices or of someone that uses the technological devices. The laws are not gender-sensitive in a way that protects victims unlike laws in France.
The organisation WOUGNET itself also experiences censorship when carrying out its work, through surveillance and monitoring by the telecommunication providers as recently as 2022. This is further exacerbated by ineffective laws in place to protect their privacy and the shutting down of organisations they partner with such as Chapter Four. Chapter Four, a civil rights organisation was shut down by the government for 9 months in 2021.
It points to a deeper problem, that is the law not empowering its civilians and shows the elevation of the patriarchy is prevalent within the Ugandan society. Elevation of patriarchal principles is further shown through a one-time Minister of Ethics (a former Catholic priest) made headlines for reference to child rape as the “right kind of rape” and called men raping girls “natural” in comparison to homosexuality (Sullivan, 2021).
One of the examples of how this deeper problem affects the women who experience cyberviolence is with reference to those in the public eye. Judith Heard, a model who experienced non-consensual dissemination of images stated “The pain never goes away” and she is constantly reminded of it because it lives on forever due to the permanence of the Internet. Both lawmakers and law enforcers are in need of the knowledge to curb the occurrence of gender and sexual cybercrime.
2.2 What activities is WOUGNET undertaking in the fight against cyberviolence?
When it comes to the fight against cyberviolence, WOUGNET executes the following activities namely research initiatives, capacity building, advocacy and awareness raising. Firstly with research, Esther mentioned that they initiated a country wide research project in 2021:
“We were privileged to have this research done in six regions of Uganda, that's north, the south, the East, the West and also the central. We looked at trying to assess online gender based violence, among the people living in the urban, rural and peri-urban as well”, (Nyapendi, 2023, p. 1).
In addition, WOUGNET carried out research to assess the rights of women online in Uganda. Such research is a major foundational block for the other activities carried out such as capacity building and advocacy and awareness raising.
Secondly, in conducting awareness raising, WOUGNET has and continues to carry out campaigns to spread information about the types of online gender based violence that can be experienced in the community as well as the impacts of these types of cyberviolence. WOUGNET's campaigns take place both online in various forms like newsletters, social media posts as well as through radio campaigns and in person interactions with art as explained below:
“…our recent initiative, we're able to use art, to tell stories of online gender based violence, depending on how people learn. We also looked at online gender based violence in schools and art was a very interesting way to kind of engage these girls and students on the subject of online gender based violence, which was quite interesting”, (Nyapendi, 2023, p. 4).
The scale and variety in the campaigns employed by WOUGNET is quite large with multiple factors taken into consideration. With a multitude of tribes and languages spoken among the people in Uganda, it is no surprise that (Internews, 2020) found that the number of licensed radio stations in March 2020 was 309. The importance of campaigns on several fronts (social media, radio, etc.) is clear when one compares the Internet penetration of the population at 40.4% with the fact that the radio is the second most popular household effect in both rural and urban households (Internews, 2020).
These kinds of activities carried out by WOUGNET which focus on providing women with the safe space to share their stories, empower the victims and do away with the culture of silence around violent experiences. Esther says;
“…we have victims that we were able to engage with, so that they can tell their story, because most of the time, they've been intimidated, their confidence has run low. So for them telling a story, and it being transformed in form of art is an initiative that WOUGNET has been able to work with in that case”, (Nyapendi, 2023, p. 4).
When it comes to advocacy for the victims, WOUGNET has set up create a toll free line for the victims to be able to report and ask questions. They also aid them in following up on their cases when engaging with the Police who may not employ the same approach as seen in 2.1.2 above. The advocacy and awareness training continually show clearly that that WOUGNET exhibits a victim first mentality similarly to Association Stop Fisha and aims to encourage their victims to regain their confidence after experiencing cyberviolence.
The third activity, which Esther referred to as capacity building takes place for both the women and the policymakers. Capacity building for women involves a two pronged approach; training the women on how to use digital technologies and then teaching them how to be safe online. This involved showing the women what settings to engage for maximum privacy on their phone and ensuring that the women who have experienced violence online are being helped to prioritize their mental health. These women in particular were referred to the practise of taking time offline (known as a digital detox) which allows them to reset and recentre themselves without being constantly reminded of the violence they have experienced online. In fact, Esther stated she would the advice to digital detox is a tip that everyone should utilise.
In capacity building for the policymakers, Esther mentions that having enlightened stakeholders aware of the different types of cyberviolence works in everyone's favour because they will create better policies that can cater to the specific types of cyberviolence being experienced.
To understand the organisation's activities within a resistance context, we will apply the (Thomas and Davies, 2005) framework from Table 3 above.
Esther states that their use of tech pop ups allows them to engage with numerous women and encourage them to innovate and advance the knowledge of online gender based violence within their communities and to explain the importance of this she adds:
“WOUGNET alone cannot do it. But if we have many women and girls in the communities that are able to extend what I should call the gospel, for lack of a better word, this knowledge of online gender based violence should be able to be dispersed into the communities.” (Nyapendi, 2023, p. 4).
Firstly, we can see that the activities conducted by WOUGNET can be defined as resistance when identified under the structural feminist perspective because each activity encourages women to speak out about their experiences in order for other women to benefit by either learning that they are not alone or becoming more aware of the gender and sexual cyberviolence.
In addition (Thomas and Davies, 2005) concluded that empowerment against resistance in this instance took shape by making the forms of oppression more visible and engaging in activities of consciousness-raising in order to turn an advantage for femaleness. WOUGNET's advocacy and work to raise awareness of cyberviolence is a direct example of this consciousness-raising.
Despite the reluctance existing within certain stakeholders such as Police because of financial resources and telecommunication companies working to preserve their own business interests, WOUGNET's activities are incredibly effective in alleviating the problem of cyber violence. The capacity building is reported to be the most effective because it allows the women to stay as safe as they can while still experiencing the benefits the internet has to offer.
2.3 Comparison
There is a difference in approaches to the portrayal of gender and sexual cyberviolence, knowledge based for WOUGNET and victim based for Association Stop Fisha.
First, Association Stop Fisha's portrayal featuring the victim based approach speaks to the existence of a strong foundational legal framework in which instances of cyberviolence are handled. It is clear in the information shared by the Association in both their book and on social media that France values the carrying of justice even with victims of cyberviolence due to clear existence of laws against these types of violence such as the Penal Code and Bills aimed at targeting hateful content on the Internet. It also has the Digital Services Act at the level of the European Union which is aimed at targeting the regulation of the cyberspace. This mechanism effectively obligates each Member State to have a designated national authority responsible for regulating social networks. These national authorities are then brought together in a permanent council at European level to ensure proper compliance with the laws in force (Pardo et al., 2022).
However, as stated earlier by (Powell and Henry, 2017), despite the importance of the law in mitigating the effects of gender and sexual cyberviolence, there is still a challenge when designing new legislation that accurately and concisely captures the harm while providing sufficient methods of redress to the victims. In addition the law may also contribute further to harms through victim blaming as evidenced by WOUGNET's experiences with knowledge gaps among stakeholders. It also asks the question of what sufficient and effective justice looks like for the victims of cyberviolence especially in situations where the perpetrator is located in another country or they conceal their identity. In this way, we understand that the organisations' activities work in tandem to reduce the effects of gender and sexual cyberviolence.
On the other hand, Uganda's society has two issues. (Powell and Henry, 2017) notes that where society is characterised by unequal power relations between men and women, these inequalities are themselves embedded in men's and women's everyday practices, including their experiences and negotiations of sexual intimacies. Such an analysis helps to explain how women's experiences of men's sexual violence are so often dismissed, tolerated or excused as normal male sexuality and ‘just sex'. The first issue is a cultural backdrop steeped in patriarchy and the other is the intertwining of conservative religious ideals of the people running the country and the laws governing the state. In this way, it is important to note that this entanglement plays a huge role in endorsing structural violence which is suffering induced by economic and political forces, such as extreme poverty, unjust healthcare policy, slum demolition (Lokaneeta, 2016). The reliance on religion and tribal culture works to further entrench the unequal footing which men and women exist in Ugandan society.
Both organisations conduct a similar litany of activities in fighting against gender and sexual cyberviolence. This is why they were both grouped under the structural feminist framework of resistance.
Recommendations
This part will briefly expand on a few recommendations for dealing with the problem of gender and sexual cyberviolence. There is no one size fits all approach for tackling a problem of its size and nature especially with the way the Internet is constantly evolving and shifting. However to begin, solutions that employ technology should be employed to deal with what is partly a technological problem.
Firstly, technological companies need to increase the effectiveness of their responses towards instances of gender and sexual cyberviolence. In a report by the Special Rapporteur on Minority Issues, they recommend the prioritization of reports by minorities in order to curb online hate speech. Similarly, social media platforms should prioritize reports made by women when they experience gender and sexual cyberviolence by being stricter with removing bad actors within these spaces. In addition, they should create mechanisms that support cooperation with law enforcement especially in instances of international cyberviolence investigations.
When Facebook (now Meta) was blocked in Uganda, it effectively crippled the opportunities of women experiencing cyber violence to receive help from law enforcers. However, even in countries where it is not blocked, platforms like Meta are reported to employ exploitation with their moderators who are the first port of call to ensure its safety across Africa (Perrigo, 2022). Exploitation of workers based in LMIC to source cheaper labour is an unfortunately common occurrence, however governments in these countries must do their part to curb this.
At government level, one of the best recommendations is to implement measures that will lessen the gender divide and access to Internet divide that may exist in low to middle income countries. For example, providing greater access to STEM opportunities specifically targeted at women. This in turn would work to encourage women's participation in the building of future platforms and work to make the presence of more women founders a reality for even low to middle income countries such as Uganda.
Another recommendation is increasing internet saturation in those areas where it is low and non-existent coupled with the training on how to engage safely and privately online. Through increasing internet saturation, the digital divide that exists can be managed and making safety a requirement from the beginning makes it ingrained in new users by design.
At a personal level, the recommendation from Esther holds true for everyone with access to the Internet. A digital detox now and then is a good way to keep grounded and centered while navigating the sometimes challenging depths of the Internet.
Further research on this topic can go a multitude of ways, into a legislative comparison of the laws that govern cyberviolence in High income and Low to middle income countries. There could be research on the perpetrators of gender and sexual cyberviolence to better understand their motives and how to put a stop to them. Another study could explore the impact on women's livelihoods after experiencing gender and sexual cyberviolence.
Conclusion
The current research aimed to examine the portrayal of gender and sexual cyber violence within the context of two organisations; a French non-profit organisation (Association Stop Fisha) and a Ugandan non-governmental organisation (WOUGNET) and to understand how cyberviolence was tackled by these organisation through their different activities.
The two research questions were as follows:
1) How do the organisations portray gender and sexual cyberviolence?
2) What activities are they employing against gender and sexual cyberviolence?
The literature review provided a background on feminism, patriarchy and resistance. It showed the history of the different waves of feminism in order to provide context to the new fight women face when participating online. It also highlighted the positioning of gender and sexual cyber violence within the patriarchy and lastly linked feminist theory to resistance. The formulation of question one arose from the finding in the literature review that the definitions of cyberviolence were used interchangeably on a regular basis and there was a lack of consensus on how to define and categorize the different types of cyber violence. Question two was formulated from the finding within the literature review that resistance was typically associated with organisations linked to blue collar workers.
Through a thematic analysis of visual and written data collected from Association Stop Fisha, a French organisation's social media accounts and book as well as an exploratory examination conducted by interview into a similar non- governmental organisation in the Global South known as Women of Uganda Network, I found that both organisations it can be concluded that despite the variance in location, both organisations have a similarity with regards to the activities they pursue in relation to the fight against cyberviolence. Their differences lie in their approach to the portrayal of gender and sexual cybercrimes which arises due to the differences in legal and societal context.
Bibliography
Aldossari, M. and Calvard, T. (2021) ‘The Politics and Ethics of Resistance, Feminism and Gender Equality in Saudi Arabian Organizations', Journal of Business Ethics [Preprint]. Available at: https://doi.org/10.1007/s10551-021-04949-3.
Backe, E.L., Lilleston, P. and McCleary-Sills, J. (2018a) ‘Networked Individuals, Gendered Violence: A Literature Review of Cyberviolence', Violence and Gender, 5(3), pp. 135–146. Available at: https://doi.org/10.1089/vio.2017.0056.
Backe, E.L., Lilleston, P. and McCleary-Sills, J. (2018b) ‘Networked Individuals, Gendered Violence: A Literature Review of Cyberviolence', Violence and Gender, 5(3), pp. 135–146. Available at: https://doi.org/10.1089/vio.2017.0056.
Beech, M. (2020) COVID-19 Pushes Up Internet Use 70% And Streaming More Than 12%, First Figures Reveal, Forbes. Available at: https://www.forbes.com/sites/markbeech/2020/03/25/covid-19-pushes-up-internet-use-70-streaming-more-than-12-first-figures-reveal/ (Accessed: 27 August 2023).
Braun, V. and Clarke, V. (2006) ‘Using thematic analysis in psychology', Qualitative Research in Psychology, 3(2), pp. 77–101. Available at: https://doi.org/10.1191/1478088706qp063oa.
Braun, V. and Clarke, V. (2013) Successful qualitative research: a practical guide for beginners. Los Angeles: SAGE.
Dickerson, V. (2013) ‘Patriarchy, Power, and Privilege: A Narrative/Poststructural View of Work with Couples', Family Process, 52(1), pp. 102–114. Available at: https://doi.org/10.1111/famp.12018.
Ebila, F. and Uhde, Z. (2020) ‘Feminist Perspectives on Social Struggles and Resilience in Eastern Africa', Gender a výzkum / Gender and Research, 21(1), pp. 3–17. Available at: https://doi.org/10.13060/gav.2020.001.
European Institute for Gender Equality (2017) ‘Cyber violence against women and girls'. European Institute for Gender Equality.
European Union Agency for Fundamental Rights (2014) Violence against women: an EU-wide survey. Main results report, European Union Agency for Fundamental Rights. Available at: https://fra.europa.eu/en/publication/2014/violence-against-women-eu-wide-survey-main-results-report (Accessed: 20 November 2021).
Goitom, H. (2021) Uganda: Constitutional Court Finds Key Sections of Anti-Pornography Act Unconstitutional, Library of Congress, Washington, D.C. 20540 USA. Available at: https://www.loc.gov/item/global-legal-monitor/2021-09-08/uganda-constitutional-court-finds-key-sections-of-anti-pornography-act-unconstitutional/ (Accessed: 26 August 2023).
Goredema, R. (2010) ‘African feminism : the African woman's struggle for identity', African Yearbook of Rhetoric, 1(1).
Instagram Help Center (no date) Copyright | Instagram Help Center. Available at: https://help.instagram.com/126382350847838/?helpref=search&query=copyright&search_session_id=918fda8d0520fb4bbe0cde8cb1c5a88b&sr=2 (Accessed: 19 August 2022).
Internews (2020) The State of Radio in Uganda, Information Saves Lives | Internews. Available at: https://internews.org/resource/the-state-of-radio-in-uganda/ (Accessed: 27 August 2023).
Kim, H. et al. (2018) ‘Evaluating Sampling Methods for Content Analysis of Twitter Data', Social Media + Society, 4(2). Available at: https://doi.org/10.1177/2056305118772836.
Lokaneeta, J. (2016) ‘Violence', in L.J. Disch and M.E. Hawkesworth (eds) The Oxford handbook of feminist theory. Oxford ; New York: Oxford University Press (Oxford books), pp. 1025–1040.
Mikell, G. (1997) African Feminism: The Politics of survival in sub-Saharan Africa. Philadelphia, PA: University of Pennsylvania Press.
Mumby, D.K. et al. (2017) ‘Resistance Redux', Organization Studies, 38(9), pp. 1157–1183. Available at: https://doi.org/10.1177/0170840617717554.
Napikoski, L. (2021) What Is a Patriarchal Society and How Does It Relate to Feminism?, ThoughtCo. Available at: https://www.thoughtco.com/patriarchal-society-feminism-definition-3528978 (Accessed: 28 August 2023).
Nyapendi, E. (2023) ‘WOUGNET Interview with Esther'.
Ortner, S.B. (2022) ‘Patriarchy', Feminist Anthropology, 3(2), pp. 307–314. Available at: https://doi.org/10.1002/fea2.12081.
Pardo, R.-F., McLaren, S.C. and Diogo, L.P. (2021) Combattre le cybersexisme. Asssociation Stop Fisha.
Pardo, R.-F., McLaren, S.C. and Diogo, L.P. (2022) Combatting Cybersexism. Unpublished.
Perrigo, B. (2022) Inside Facebook's African Sweatshop. Available at: https://time.com/6147458/facebook-africa-content-moderation-employee-treatment/ (Accessed: 28 August 2023).
Powell, A. and Henry, N. (2017) Sexual Violence in a Digital Age. London: Palgrave Macmillan UK. Available at: https://doi.org/10.1057/978-1-137-58047-4.
Samuel, A. (2017) Finding the Words We Need to Talk About Sexual Assault and Harassment, JSTOR Daily. Available at: https://daily.jstor.org/the-vocabulary-primer-you-need-for-talking-about-sexual-assault-and-harassment/ (Accessed: 26 August 2023).
Statista Search Department (2022) Biggest social media platforms 2022, Statista. Available at: https://www.statista.com/statistics/272014/global-social-networks-ranked-by-number-of-users/ (Accessed: 26 August 2022).
Stop Fisha (2023) ‘Our History – Stop Fisha | Stop Fisha'. Available at: https://stopfisha.org/stopfisha-notre-histoire/ (Accessed: 19 August 2023).
Sullivan, G. (2021) ‘Ugandan official wants to arrest victim of revenge porn: “She should be locked up and isolated”', Washington Post, 26 October. Available at: https://www.washingtonpost.com/news/morning-mix/wp/2014/11/12/ugandan-official-wants-to-arrest-victim-of-revenge-porn-she-should-be-locked-up-and-isolated/ (Accessed: 26 August 2023).
Tenny, S. et al. (2022) ‘Qualitative Study', in StatPearls. Treasure Island (FL): StatPearls Publishing. Available at: http://www.ncbi.nlm.nih.gov/books/NBK470395/ (Accessed: 18 August 2022).
The European Union Intellectual Property Observatory (2022) FAQs on copyright for consumers. Available at: https://euipo.europa.eu/ohimportal/en/web/observatory/faq-fr#faqanchor_FR (Accessed: 19 August 2022).
Thomas, R. and Davies, A. (2005) ‘What Have the Feminists Done for Us? Feminist Theory and Organizational Resistance', Organization, 12(5), pp. 711–740. Available at: https://doi.org/10.1177/1350508405055945.
Wajcman, J. (2004) TechnoFeminism. Cambridge ; Malden, MA: Polity.
Walters, M. (2005) Feminism: A Very Short Introduction. New York: Oxford University Press.
Wilk, A.V.D. (2018) ‘Cyber violence and hate speech online against women'.
Women in The World Foundation (2023) Women of Uganda Network (WOUGNET) | Women in the World Foundation. Available at: https://womenintheworld.org/solutions/entry/women-of-uganda-network-wougnet/ (Accessed: 19 August 2023).
WOUGNET et al. (2016) ‘Women's Rights and the Internet in Uganda – WOUGNET'. Available at: https://wougnet.org/download/womens-rights-and-the-internet-in-uganda/ (Accessed: 27 August 2023).
WOUGNET (2023) WOUGNET – Women and ICT. Available at: https://wougnet.org/ (Accessed: 19 August 2023).
Yin, R.K. (2018) Case study research and applications: design and methods. Sixth edition. Los Angeles: SAGE.
APPENDIX
Qualitative Interview Guide – WOUGNET
Explanation of the dissertation and its aim:
I am a final year Master's student of Digital Law and Management from ESDES Lyon Business School. I decided to carry out a cross cultural enquiry into the treatment of gender and online gender based violence in France and Uganda. I already gathered my data from France. For Uganda, I decided to interview a person/ people from a similar organisation i.e. non-profit and fighting against online gender based violence in order to better understand the similarities and differences in portrayal, activities against online gender based violence.
- Introduction of the role
Here, we require some details/projects about the work they have participated in within the context of the organisation
– In what capacity do you work at the organisation?
- Trends of online gender based violence
Comparison points for trends can include women in rural vs urban areas, younger women vs older women.
– What trends have you identified in the online gender based violence against women in Uganda?
- Specific types of online gender based violence
Here it is important to gauge how they define the different types of gender based violence they mention and understand which ones they see most within their work in the organisation
– Which specific types of online gender based violence would you say are most prevalent?
- Actions/activities against online gender based violence
– What activities is WOUGNET taking against online gender based violence in Uganda?
- Effectiveness of activities against online gender based violence
– Would you say these activities are effective against online gender based violence?
– How is their effectiveness measured?
WOUGNET Interview with Esther Nyapendi (Julian, 2023)
Julian: So, is it okay if I record this?
Esther: Sure, I'm okay with it
Julian: Okay, okay. Cool. So, please tell me in what capacity do you work for Women of Uganda Network?
Esther: So my name is Esther Nyapendi. For the record, I work with Women of Uganda Network as the Assistant Technical Support Officer. And I also work as a digital literacy and security trainer. I've also led various projects that WOUGNET is handling.
I lead various programs, for instance, for the ending online harassment amongst women journalists. And currently I'm leading a project called Smile. And it works to you know, provide capacity, technological devices, internet and data for our member organizations.
Julian: Okay. That's really wonderful. Thank you so much for that very, very clear explanation. So I just wanted to get into my questions. And I'll let you talk a lot of the time because I want you to really emphasize and kind of get into details about what you do, and the activities as well. So my first question is what are the trends that you have identified in online gender based violence against women in Uganda?
Esther: For us specifically from our research, and I really want to quote the research that we did in 2021 to assess the types, forms, the impacts of online gender based violence amongst women and girls. And we were privileged to have this research done in five regions of Uganda, that's the north, the south, the east, the west and also the central. We looked at trying to assess online gender based violence, among the people living in the urban, the rural areas and peri – urban as well.
So, some of the forms that we looked at that women face included online stalking. This was a very common form of online gender based violence that, most women face. We looked at the non-consensual distribution of intimate images. This was majorly done by the intimate partners. Over time we've looked at examples of, Desire Luzinda, we've looked at Linda Dane. These are women in Uganda that have faced the non-consensual distribution of intimate images, and they have been greatly affected by this.
Another one is the online grooming, this one usually occurs mostly to women, because, they are found to be vulnerable. We defined online grooming as, tricks or, pressure that women face, or are tricked into, sexual activities. On that note, personally I've faced online grooming because, someone texts you on, let's say, for instance, Facebook and asks you to share naked videos of yourself or pictures, or even them themselves, share these images to intimidate you. So we also looked at cyber bullying, doxxing, which usually occurs on Twitter. Someone just constantly sending you messages, and intimidating you. We looked at trolling. This is very common, for instance, on Twitter, when people are hashtagging you. So in some of the cases that we interviewed women, they talked about trolling, as an activity that someone hashtags, your name. So one of it is an example of a lady that we interviewed, talked about how her pictures were linked on Twitter, and she was being hashtagged. When she woke up in the morning, there were tons of hashtags about her name. That really got scary for her. So with that, I'll mention those.
Julian: Thank you so much for answering that question. Because you answered another one of my questions through that explanation. So when I said trends, I wanted for example, you said that you guys did research and you interviewed women in the north, the south, urban areas, rural areas. For example, did you notice things like the women in in the urban areas experienced more online gender based violence, mainly because they have easier access to smartphones? Or did you notice one specific type of based online gender based violence was more prevalent with women in rural or urban areas? Or did you notice something else that specifically stuck out with with all the different types that you mentioned? So you mentioned stalking, non-consensual distribution of intimate images, online grooming, doxxing and trolling? So which one would you say happens most prevalently in Uganda?
Esther: I think to just kind of narrow it down, women in urban areas face more attacks than women in the rural areas, simply because there is access to technology. They have the mobile phones, they have internet access compared to the women in the rural areas. Also in the scenario that women in the rural areas had faced online gender based violence, they did not even know that online gender based violence was a type of violence that they should report about. So that was the challenge that was there.
Julian: Okay. Thank you for the clarification. So then can you expand upon the activities that Women of Uganda Network has been carrying out against online gender based violence? I know. Sorry. Sorry, go on.
Esther: Okay. So first to mention, which we've really talked about is the research. WOUGNET has carried out a series of research to assess the types, to also assess the rights of women online. And that has really helped to inform the work that we do, and other organizations as well. Another one is advocacy and awareness raising. With this, WOUGNET has carried out online campaigns to share information about online gender based violence in form of informing the community about the types of online gender based violence. Because a scenario that regularly occurred is some of the women didn't know how to differentiate between which type of online, harassment/violence they are facing. That also is a challenge when they report to the police and the police cannot help in that matter, because if someone comes and says, “I'm facing online harassment”, and yet it's cyber bullying, then the police cannot be able to help specifically to solve the matter.
So WOUGNET has worked to ensure that there is more advocacy and awareness raising that is done to inform the communities about the impacts of online gender based violence, about the spread of online gender based violence, and that really has, caused the issue to be known to our community. Another one is capacity building. Being digital literacy and security trainer, the experience has been informing more and training more women and girls on how to use ICT, especially for the rural areas. It's more of training them how to use the technology, and then later on teaching them how to be safe online, compared to the urban areas, where the knowledge they have on how to use these technologies is quite on a higher level. And so most of it is ensuring that they are aware that their security and safety is in check. And for security, you are majorly teaching them about how to ensure that their privacy on their mobile devices is activated, ensuring that their settings are right now, while for safety, we've looked at ensuring that the victims of online gender based violence are being helped for their mental health. And in that case, that they are being referred and also encouraging them to take some time off social media so that the matter cools off. I think that's basic advice to give to a victim of online gender based violence.
Okay, we also have been able to engage in various initiatives, our recent initiative, we're able to use art, to tell stories of online gender based violence, depending on you know, how people learn. We also looked at online gender based violence in schools and art was a very interesting way to kind of engage these girls and students on the subject of online gender based violence, which was quite interesting. And still on the storytelling part, we have victims that we were able to engage with, so that they can tell their story, because most of the time, they've been intimidated, their confidence has run low. So for them telling a story, and it being transformed in form of art is an initiative that WOUGNET has been able to work with in that case. We also look at initiatives like tech pop ups where we engage very many girls to kind of come out and use technology and be creative and be innovative in certain ways so they can advance the subject of online gender based violence in their communities. So in a matter that WOUGNET alone cannot do it. But if we have many women and girls in the communities that are able to extend what I should call the gospel, for lack of a better word, this knowledge of online gender based violence should be able to be dispersed into the communities. Because the scenario, often even when we've carried out the research is that even for the women in the urban areas, most of them do not know that, online harassment or online gender based violence is a kind of violence that they deserve justice for.
So another thing that WOUGNET is doing is policy engagement, because it starts from the law. And then people are aware that, when I face online gender based violence, I can be able to report and the perpetrators can be able to pay for what they have done. So we have been able to engage with the government, the policy makers, the law enforcement, to really kind of give them a view of what gender specific laws should be in the laws that are already existing. Now, for instance, the examples of the laws that we have, the Computer Misuse Act is really broad and ambiguous and does not have specific areas that look at specific types of online gender based violence. For instance, the Computer Misuse Act does not specifically look at online violence, or cyber stalking, so, that becomes a challenge when victims report to the police, and they do not have a direct way to help them because the law then does not look at specific types of violence. And that brings me to the high level dialogues that WOUGNET has with different stakeholders, and one of the initiatives that we had was creating a toll free line, that victims can be able to report their questions to WOUGNET and then WOUGNET can be able to look out for different networks and support services. For instance, when a victim reports the case to our organization, we are able to refer them to the police and also follow up that they have been helped, because that's always a challenge that women face, or girls or victims of online database violence. That once they go to the police and report, there are either questions of “What were you doing online? Why did you post that image?” So, there's that kind of censorship that comes about when someone knows that they cannot be helped. So they are not able to freely access information, their freedom of expression is compromised. So we look at ensuring that most of this violence is not physical, as we as we have been looking at it, and most of the impact that it has created is psychological effects and emotional, so you realize that, they are intimidated. An example of Judith Heard when we interviewed her, she said “That pain never goes away”. Once someone faces that kind of harassment and the whole world knows about it, because she is a model and she's known by so many people that it's a constant referral of the internet reminding her because the internet definitely records any information that is posted there for God. So even up to now, when you check upon those people, that information is still there and that keeps on reminding them. An example of Fabiola she was fired from her job. So the impact of online gender based violence, violence and what WOUGNET is doing is to really give that psycho support to victims of online gender based violence.
Julian: Okay. Thank you so much. That was really, really, really helpful and really thorough. I wanted to also ask, so would you say that these activities are effective in their aim? Okay, I'm going to assume that your answer is yes. But what would you say has been the most effective, and why?
Esther: I think what's been more effective is the capacity building because what we have been able to do is train the women and girls on how to be safe online. And also, we have been able to train the stakeholders, as well on these matters, especially you realize that with the police, they are people that this violence is being reported to, but if they do not have the capacity, they are not going to be able to handle these cases, and it's still a challenge, for the different stakeholders, because they have not known that online violence is violence, and the perpetrators of this online violence, should be able to be punished. And because the internet also has aspects of anonymity, where there is impersonation, someone creates an account and shares information or bullies, another person, the police has not yet looked at how to find those perpetrators.
So, capacity building, especially for the women and girls, also the different stakeholders, has been able to enlighten or make them aware of the matter. And that also helps them in the policies that they're making on how to handle these cases of online violence, because it differs from someone who's being cyber bullied and someone who is being cyber stalked. And we've had cases where online harassment has transitioned to the offline harassment. Someone starts with stalking you online and when you're not responding or you block them, they start to follow you physically, because they've, had traces of information that they've collected, they know where you stay, and all those other things. And so that looks at that aspect of capacity building. But you know, the challenge has always been lack of resources, and also to talk about the law. Capacity building in terms of how they can safely use devices, and also capacity building on what laws are available for women to use once they face this online gender based violence or online violence. Because in the matter, for instance, a law that we have on Anti-Pornography, 2019, the Anti-pornography law looks at an aspect and this is a challenge that when someone posts, for instance, my intimate images, I am the one that is being affected. And so the law does not actually look for the one that posted them, but I am being affected. So that, has also been a challenge. Capacity building has been also looked at it in two perspectives on digital security and safety and the law as well.
Julian: Okay, thank you so much. But that's actually really, really clear. I liked what you mentioned, the specific laws that you were talking about, because I did have just a little bit of knowledge about the about the laws, but then I didn't really know them to that extent. But thank you for being specific about that. Actually, you mentioned something I wanted you to kind of touch on a little bit more. So the challenges, you spoke a little bit about lack of resources. But can you identify any other challenges that you guys are currently facing?
Esther: Yes, then the another challenge that we're kind of facing is the lack of awareness and understanding on the issue of online gender based violence. And from what I previously mentioned, from the research we conducted, we realized that some of the women and girls in the community at large do not actually know that they are facing online gender based violence. And so to say when they face, some of the responses we got were that they just ignore it until it really escalates to the high levels, that's when they kind of become inquisitive to what is happening and how they can ask for help and all that. Another one I could mention is the Internet itself being a tool that we all need information from. And it's still a tool that is not safe for us because you realize that with different applications developed and all that, you realize that for instance the social media applications that we use, yes, we can be there to access information, be updated on the news. But once we are violated, online, these social media platforms cannot be able to help us. An example could be the shutdown of the internet and Facebook that occurred in 2021 during elections and till date, Facebook is blocked. So the challenge is, it was a platform that very many Ugandans used for business. And they still want to use it for business, because there's a diverse kind of population that's there. You realize that till date, Facebook has been closed, and once you face online harassment and violence on that application, you cannot be helped, because the question is, “It was blocked in Uganda, what were you doing there?” So, we have not been able to get support from social media platforms in that regard. And also to talk about the law, the challenge is that we are being surveilled as an organization, that alone really is a challenge for us, because then we cannot help out individuals that are facing online harassment. Different internet service providers in Uganda, we use Airtel and MTN, they do not have policies that protect our privacy. Because we use their internet to do the work that we do. So that alone is a challenge to us. In 2022, the government was using the internet service providers to surveil and monitor the activities that organizations are doing, and we had cases of temporary closure of organizations, for instance UWONET (Uganda Women's Network) Chapter Four, and yet you realize that we collaborate with them to handle cases of online gender based violence. So that's a case that there is no that level of privacy and data protection in that matter. Also what I mentioned, is the laws are being very ambiguous, they are not specific. I mentioned the Anti-Pornography Law and the Computer Misuse Act, they really need to be worked on. They need to be gender sensitive, and responsive.
Julian: Okay. Gender sensitive. And could you elaborate on that? So yes, what do you mean by gender sensitive?
Esther: I'll give you an example. For instance, the Computer Misuse Act in Uganda just looks at technological devices or someone using technological devices to perpetrate others. But then it does not kind of have the data that you know, women are the ones that are mostly affected. It doesn't look at the kind of help and safety that women need to use online tools. So in some of our initiatives, we've been able to talk with policymakers to kind of make the laws gender sensitive.
Julian: Okay. I have another question. Just going into the tangent of making the laws more gender sensitive. So would you say that there the laws provide adequate protection for children? Or would you say differently?
Esther: Yes I would say the law does not offer adequate support to the children.
Julian: Okay. Do you have anything else to add with regards to challenges?
Esther: Oh yes. In regards to the challenges, still we'll talk about the stakeholder engagement among the different parties that are supposed to work on ending online gender based violence.
It's still a reluctant kind of way that they are acting. For instance, the Police are still reluctant because for them to be able to look at these matters they need money. Another aspect is that the internet service providers still don't want to engage in that matter because for us in Uganda and because we do not have laws that govern that body, they still do not want to engage and learn on the issues of online gender based violence because for them on their side, it's a business entity. When they look at that, they draw away. And we've had cases where we've invited them and one person shows up and they can't actually share the status of these things. They don't have policies that govern data protection and all that so it's quite a challenge. And generally in Uganda, online gender based violence is still not looked at as a form of violence. So WOUGNET as a whole, is looking towards the agenda of different other stakeholders ending online harassment
Julian: So how do you measure the effectiveness of your activities? Is it through the research or surveys?
Esther: Ah yes, what usually happens is that from the impacts that women usually face. For instance, the censorship we look at increasing more women to use online platforms. The scenario is usually they are censor away from using the internet and online applications. But from what we use to measure is the increased number of women that can be able to speak and also participate in online engagements. Yes, that's a major kind of card that we use to ensure that the activities we do are really effective.
Julian: That was my last question. If I have any follow ups, do you mind me sending you an email?
Esther: Yes you can. Let me type my email in the chat.
Title of the dissertation:
Gender and sexual cyberviolence: an exploratory cross-cultural inquiry
Central Question:
As new ways of existing online come into being, so do the ways in which women are being oppressed and abused on the internet. An examination of two organisations with different contexts, one in Europe and another in the Global South led to two research questions:
1) How do the selected organisations portraying gender and sexual cybercrime?
2) What activities are the organisations carrying out against gender and sexual cybercrime?
Summary:
Gender and sexual cyberviolence, which can also be referred to as online gender based violence is a widespread problem given the ever expanding size of the internet and its increased use in our day-to-day lives. The ever shifting nature of the internet has birthed a new extension of the oppressive systems and practices in place against women. The first part of this paper is a literature review featuring a historical overview of the different waves of feminism throughout the years along with a contextual positioning of gender and sexual cyberviolence in relation to patriarchy, the counter to feminism's propositions. In addition, it will feature a brief insight into resistance from an organisational perspective. The literature sets the stage from which to examine the difference in portrayal of gender and sexual cyberviolence as examined from two organisations, one a high income country located in Europe (France) and the other a low to middle income country located in the Global South (Uganda).
For the field study, the research methods chosen were data analysis of a book and social media data and interview. The book was written by the members of one of the organisation and the social media data was collected from their different social media accounts. The interview was conducted with an employee of the other.
The results from the data analysis and interview show a difference in the approach to portrayal by the two organisations. Both approaches are useful in fighting against gender and sexual cybercrime and remind us to consider the organisation's legal and societal context when contemplating the organisations' activities. It is important to note that this study is an introductory inquiry and thus can be expanded in further studies in a multitude of ways.
Key words: feminism – internet – women – Uganda – France
Titre du mémoire:
Cyberviolence sexuelle et à caractère sexiste : une enquête exploratoire interculturelle
Rappel problématique : Comme de nouvelles façons d'exister en ligne apparaissent, les façons dont les femmes sont opprimées et abusées sur Internet évoluent également. L'examen de deux organisations avec différents contextes, l'une en Europe et l'autre dans le Sud global, a conduit à deux questions de recherche :
1) Comment les organisations sélectionnées représentent-elles la cybercriminalité sexuelle et à caractère sexiste ?
2) Quelles activités les organisations mènent-elles contre la cybercriminalité sexuelle et à caractère sexiste ?
Résumé :
La cyberviolence sexuelle et à caractère sexiste, qui peut aussi être appelée la violence en ligne basée sur le genre, est un problème très répandu étant donné la taille sans cesse croissante d'Internet et son utilisation accrue dans notre vie quotidienne. La nature toujours changeante d'Internet a engendré une nouvelle extension des systèmes et pratiques oppressives en place à l'encontre des femmes. La première partie de cette étude est une revue de la littérature comprenant un aperçu historique des différentes vagues du féminisme au fil des années ainsi qu'un positionnement contextuel de la cyberviolence sexuelle et à caractère sexiste en rapport avec le patriarcat, à contre-courant des propositions du féminisme. De plus, il comprendra un bref aperçu de la résistance d'un point de vue organisationnel. La revue de la littérature paver la voie pour l'examen de la différence dans la représentation de la cyberviolence sexuelle et à caractère sexiste telle qu'elle est examinée par deux organisations, l'une fait partie d'un pays à revenu élevé situé en Europe (la France) et l'autre fait partie d'un pays à revenu faible ou intermédiaire situé dans le Sud global (Ouganda).
Pour l'étude sur le terrain, les méthodes de recherche choisies ont été l'analyse des données d'un livre, des réseaux sociaux et des interviews. Le livre a été écrit par les membres de l'une des organisations et les données des réseaux sociaux ont été collectées auprès de leurs différents comptes sur les réseaux sociaux. L'interview a été réalisée avec un employé de l'autre organisation.
Les résultats de l'analyse des données et des interviews montrent une différence dans l'approche de la représentation par les deux organisations. Les deux approches sont utiles dans la lutte contre la cybercriminalité sexuelle et à caractère sexiste et nous rappellent de tenir compte du contexte organisationnel au moment d'envisager les activités des organisations. Il est important de noter que cette étude est une enquête introductive et peut donc être développée dans des études ultérieures de nombreuses manières.
Mots-Clés : féminisme – internet – femmes – Ouganda – la France
PBJ Learning Review
This is such an amazing paper, I just can't stand it.
Honestly, I was chilled to the bone through most of this dissertation, and it was a hard read, emotionally. I got caught up a few times. I only made it through all of it because I was doing a lot of cutting and pasting and reading everything carefully as I dropped it into the correct place, and taking breaks from time to time.
The internet is dangerous. This inadvertently explains in great detail just how dangerous it is and will help you understand the murky world all your children and parents inhabit while on the Internet.
How can a parent just give their kid “a phone” without understanding all of this? I don't get it.
If you choose to read this, you will:
Learn the underlying issues behind why it's dangerous. Understand why a standardized legal lexicon is important, particularly since we are entering into an age of “technology-facilitated sexual violence” and international crime.
You'll learn so much about cyberviolence.
“Broadly speaking, the concept of cyberviolence is meant to encapsulate the kinds of harm and abuse facilitated by and perpetrated through digital and technological means. The UN's adoption of the term in their 2015 Cyber Violence Against Women and Girls (VAWG) report brought about debate about the definition of cyber VAWG, because of its terminological overlaps with other forms of violence and crime, and the extent to which the term's attempt to capture all forms of online violence was either accurate or fair (Chisholm, 2006).”
“In their review, (Backe et al., 2018) held that there was a lack of consistent, standard definitions or methodologies used to conceptualize and measure cyberviolence. Most of the literature focuses on cyberbullying among heterosexual adolescents in high-income countries. Demographic data on perpetrators are limited, prevalence estimates are inconsistent, and almost no primary research has been conducted in low- and middle-income countries (LMIC). Cyberviolence is not only associated with negative psychological, social, and reproductive health outcomes but also it is linked with offline violence, disproportionately affecting women, girls, and sexual and gender minorities. There is an urgent need to develop a uniform set of tools to examine cyberviolence internationally. Future research should explore the gendered dimensions of cyberviolence and the continuum between online and offline violence, including in LMICs. (Backe et al., 2018) suggest that the various terminologies used to describe cyberviolence are similar but not necessarily interchangeable (IGF 2016), demonstrating a lack of consensus within the research community on how to define and categorize these digitally based behaviors and actions. The result is an intermeshing of categories following which they created a table showing the breaking down of the different forms of cyberviolence as shown on the next page.”
You'll learn the terms related to it.
And just like the internet, you'll learn that some of the terms are absolutely disgusting. My mind was blown.
This put a lot of things into perspective for me. For instance, it makes the dangerous experience of a young child with unfettered access to the Internet, in the privacy of their own room, seem as real to me as any horror movie I can imagine.
Please educate yourself and your children about the dangers of the Internet. Take Human Trafficking Essentials right now for any price you choose.
Bravo, Julian. Bravo!
Billy Joe Cain
Co-founder, PBJ Learning
Executive Director, Radical Empathy Education Foundation
